The COSO Enterprise Risk Management Framework recently issued new guidance, “ Managing Cyber Risk in a Digital Age”, that brings cyber risk quantification close to the core of the most widely used ERM framework. The document specifically recommends FAIR™ (that’s Factor Analysis of Information Risk, the model operationalized on the RiskLens platform) for quantifying risk and setting risk tolerance (see page 9), but the financially defined, businesslike approach to cyber risk of FAIR and RiskLens underpins all the guidance in the new document, which is aimed at boards of directors, audit committees, executives and risk managers.
The RiskLens platform and an overall quantitative cyber risk management program can help organizations meet each of the 20 principles from the five categories in the guidance document. For starts, we mapped 10 of the ways that RiskLens product and program features fulfill the principles.
For background and more detail, see my blog post for the FAIR Institute: How FAIR Can Ensure the Success of COSO Risk Management Programs
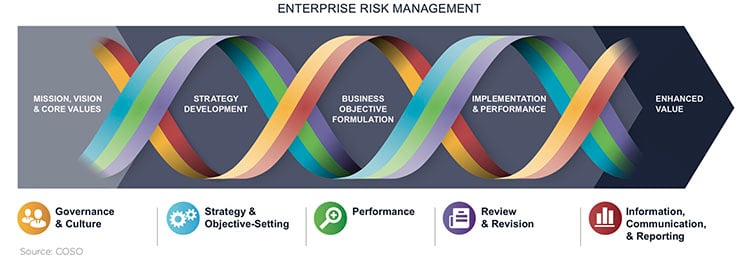
COSO’s 5 Categories of ERM
PRINCIPLE 1. EXERCISES BOARD RISK OVERSIGHT
"The board of directors provides oversight of the strategy and carries out governance responsibilities to support management in achieving strategy and business objectives."
RiskLens cyber risk reporting in financial terms shows the board the top cyber risks and sets cyber in context of enterprise risk management, giving the board a firm basis to evaluate management's effectiveness in achieving business objectives in cyber risk management.
Resource: You Can Have Answers by Your Next Board Meeting
PRINCIPLE 7. DEFINES RISK APPETITE
"The organization defines risk appetite in the context of creating, preserving, and realizing value."
With the guided RiskLens approach, and applying risk quantification, organizations can explicitly define a measured risk appetite, avoiding confusing subjective qualitative terms, and then consistently evaluate cyber risk against appetite through analysis on the RiskLens platform.
Resource: How to Set a (Meaningful) Cyber Risk Appetite with RiskLens
PRINCIPLE 8. EVALUATES RISK MITIGATION STRATEGIES
"The organization evaluates alternative strategies and potential impact on risk profile." Run cost-benefit analyses with the RiskLens platform to compare proposed mitigation projects and evaluate the effectiveness of the overall security program in risk reduction.
Resource: Admit It. You Don’t Really Measure Your Cybersecurity ROI
 More recognition of FAIR by standards bodies: The popular NIST CSF cybersecurity framework now includes FAIR as an “informational resource” for risk assessment and risk management. Learn more about NIST CSF and FAIR.
More recognition of FAIR by standards bodies: The popular NIST CSF cybersecurity framework now includes FAIR as an “informational resource” for risk assessment and risk management. Learn more about NIST CSF and FAIR.
PRINCIPLE 10. IDENTIFIES RISK
"The organization identifies risk that impacts the performance of strategy and business objectives."
RiskLens allows users to quickly identify the probable loss events based on the FAIR standard taxonomy and analysis model. Once probable loss scenarios are defined, RiskLens helps users to conduct rapid risk assessments in minutes and automatically rank them in order of significance.
Resource: RiskLens Unveils a New Triage Function for Rapid Risk Quantification 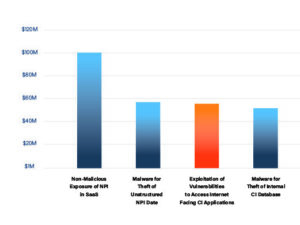
PRINCIPLE 11. ASSESSES THE SEVERITY OF RISK
"Cyber risks are evaluated against the possibility that an event will occur and adversely affect the achievement of the organization’s objectives...Responses must be made upon relevant, quality information that prioritizes funding to the information systems that are the most critical to the entity."
RiskLens analysis, based on the FAIR standard, evaluates potential loss events on probable frequency of occurrence and magnitude of impact – and identifies crown jewel assets and systems presenting the highest risk of loss in financial terms.
Resource: In a Top-10 Risks Analysis, Get These 2 Factors Right: Frequency and Magnitude
PRINCIPLES 12 & 13. PRIORITIZES RISK AND RISK RESPONSE
“The organization assesses and prioritizes risks … to design controls and other risk responses that are highly effective in minimizing the disruption of potential cyber attacks and keeping highly valued assets secure.”
The RiskLens platform acts as a decision support platform which provides a solid foundation for prioritization of cyber risk in financial terms and evaluating the effectiveness of various responses (the “4 T’s”) based on probable risk reduction, also in financial terms.
Resource: How to Prioritize Your Cybersecurity Program Based on Risk
PRINCIPLE 14. DEVELOPS A PORTFOLIO VIEW
“The portfolio view of risks should be updated on a continuous basis to reflect changes that could impact an organization’s deployment of cyber risk management activities to protect its most critical information systems.”
The RiskLens platform both aggregates and communicates cyber risk related to critical business views (departmental, geographical, functional) across the organization - and provides individual asset owners with views of their own cyber risk, as part of the RiskLens Risk Portfolio product. RiskLens also integrates with major GRC and IRM platforms.
Resource: Don’t Know Your Top Risks? Read This Mini-Guide to Start

PRINCIPLE 16. REVIEWS RISK AND PERFORMANCE
"Assurance on control effectiveness related to cyber risk (i.e. how risk controls are periodically monitored and tested) can be performed by the internal audit department or by an external auditor for independent reporting purposes."
Audit teams can leverage RiskLens to evaluate the significance of out-of-compliance conditions and help the cybersecurity teams to prioritize their corrective actions based on business significance. This is especially important as the sheer number of findings most often exceeds the amount of resources available which makes prioritization even more important.
Resource: How IT Auditors Evaluate the Effectiveness of Controls with Risk Quantification
PRINCIPLES 17 & 18. IMPROVES ERM & LEVERAGES IT TO SUPPORT ERM
“To mitigate the risk of a successful cyber attack, organizations should develop processes to identify and assess how a significant change would influence strategy, business objectives, and risk appetite…Organizations leverage data from multiple technology systems as inputs to support ERM."
RiskLens helps integrate cyber into ERM by implementing a common risk taxonomy and quantification model consistent with the other risk management disciplines – and functions as an integrated risk management (IRM) solution. The RiskLens platform leverages data from both internal IT systems and industry data (such as threat tables and loss tables) as inputs for analysis.
Resource: Cybersecurity HAS Joined ERM
PRINCIPLE 20. REPORTS ON RISK & PERFORMANCE
“An organization must implement a clearly defined process for relevant and timely reporting at various levels…Similarly, being able to communicate with external stakeholders on cyber related matters is equally as important."
The RiskLens platform generates risk reports that provide a detailed understanding for the board on the types and severity of cyber events. This risk-based reporting also meets the disclosure requirements of the SEC, New York DFS, GDPR and other regulators and stakeholders.
Resource: Five Promises You Can Make to Your Board on Cyber Risk