 Business Email Compromise (BEC), like most cyber threats, has only become more prominent as attackers continue to evolve and improve at it.. Microsoft recently broke up a large-scale BEC campaign that used cloud-based infrastructure to target mailboxes to intercept financial transactions. The FBI reports business email compromises at nearly $2.4 billion in 2021. In this post, we’ll talk about how to use RiskLens and FAIR to quantify BEC scams and greatly improve email risk management.
Business Email Compromise (BEC), like most cyber threats, has only become more prominent as attackers continue to evolve and improve at it.. Microsoft recently broke up a large-scale BEC campaign that used cloud-based infrastructure to target mailboxes to intercept financial transactions. The FBI reports business email compromises at nearly $2.4 billion in 2021. In this post, we’ll talk about how to use RiskLens and FAIR to quantify BEC scams and greatly improve email risk management.
What is Business Email Compromise?
What is Business Email Compromise?
Business Email Compromise (BEC) is a type of social engineering attack that, according to the FBI, starts with a criminal sending an email that appears to come from a legitimate source with a legitimate request. BEC attacks can occur through different means, but the most common are related to social engineering email attacks and spear phishing or man-in-the-middle phishing attacks. The cyber-criminal usually is trying to get money or information for use against an organization or an employee.
Even though email is the most common means of communication for this type of attack, there are different ways criminals use email to conduct BEC scams. According to the FBI, there are five types of BEC scams that most commonly affect organizations:
- CEO Fraud: The attacker(s) positions themselves as the CEO or executive of a company and emails an individual (typically within the finance department) with a request for funds to be transferred to an account controlled by the attacker(s).
- Direct Deposit/Payroll Diversion Scam: A criminal attempts to contact targeted HR and payroll staff, pretending to be a current employee who needs to update banking details for direct deposit.
- Tax Form Scam: The threat actor targets HR or accounting team members and requests W2 details for the organization’s staff. The purpose is to gain the personal identification information of employees to either steal identities or submit false tax returns in order to obtain the associated tax refunds.
- False Invoice Scheme: Attackers commonly target foreign suppliers with this tactic. The scammer acts as if they are a supplier and requests fund transfers to fraudulent accounts.
- Data Theft: An attacker targets HR employees (usually) in an attempt to obtain personal or sensitive data about individuals within the company, especially high-level executives. This data can then be leveraged for future attacks such as CEO fraud (see above).
Learn more about BEC attacks through the FBI’s Internet Crime Report.
Quantifying Business Email Compromise Risk with FAIR™ and RiskLens
In 2021, the FBI’s Internet Crime Complaint Center (IC3), recordedr 847,376 complaints regarding BEC with a potential loss of more than $6.9 billion across multiple industries.
There’s no question that your organization is at risk; if your organization uses email, it has some level of email security risk. The questions are, “What’s your probable loss exposure?” and “What’s the appropriate level of security investment?” Factor Analysis of Information Risk (FAIR) analysis, the international standard for quantifying cyber risk in financial terms, run through the RiskLens platform, can give you the answers.
Let’s walk through the analysis of a BEC risk scenario. We’ve picked a common one that we’veexperienced in Threat Intelligence Analyst. We’ve gone ahead and identified the asset, threat, and effect below along with a loss statement.
Asset: Accounting Application
Threat: External Malicious Actor
Effect: Integrity
Loss Statement: Assess the risk associated with an external malicious actor convincing a privileged insider via social engineering to alter vendor payment data in the accounting application.
Frequency: How often do we expect an external malicious actor to attempt to convince a privileged insider to alter vendor payment data in our accounting application via social engineering?
Magnitude: How much financial loss do we expect to experience each time this event occurs?
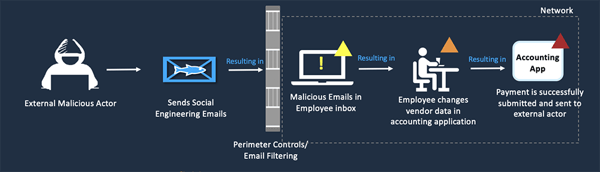
Below is an example attack chain, which is a simple way to demonstrate how an external malicious actor would attempt to use an insider to alter data in accounting applications.
Figure 1: Example Attack Chain
Event Frequency
Utilizing an attack chain is extremely helpful to clearly articulate how you suspect the event to unfold when speaking to SMEs and gathering data. Attack chains make it clear how a security risk can be exploited, which makes it easier to pin down exactly where the danger is. Some questions to consider during this stage are:
- Has our organization experienced a business email compromise attack in the past?
- How many phishing campaigns are reported in our organization, per year?
- Are there any controls that would prevent a malicious/phishing email from landing in an employee’s inbox?Once the email is in the employee’s inbox, is there anything that would prevent the employee from successfully altering data?
You can also begin to think about how to address email risk at this stage. In the case of email threats, you might consider separation of duty controls, where each part of the process to alter data and confirm receipt must be signed off by different individuals, as a way to reduce the risks of email fraud.
Event Magnitude (Financial Loss)
We consider these likely ways that loss would occur:
- Incident Response Management
- Affected Party (i.e., Customer) Notification
- Regulator Notification
- Credit Monitoring Provided to Affected Parties
- Litigation Cost/Regulatory Fines/Settlements'
We derive the values for these losses by answering questions in interactive workshops on the RiskLens platform.
Current State of Financial Risk
With data in hand, we can run an analysis on the platform showing our current level of probable loss exposure from Business Email Compromise.
Figure 2: Example Reporting

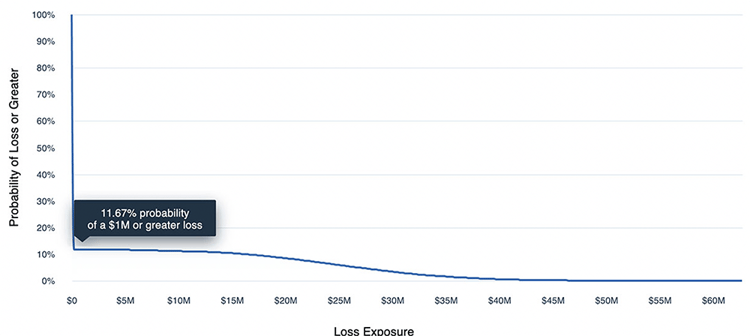 The report shows financial loss exposure on both an annual and per-event basis, as well as how likely an event is to occur.
The report shows financial loss exposure on both an annual and per-event basis, as well as how likely an event is to occur.
Please note: The results above are for example purposes only and are not meant to represent the scoped scenario for BEC.
Evaluating Risk Reduction Alternatives for BEC
Below are some examples of potential risk reduction options we can consider. Then, we can use the RiskLens platform to determine how they will affect risk by reducing event frequency or loss magnitude.
-
Increased employee training/awareness
-
New/enhanced Identity Access Management controls
-
New/enhanced Data Loss Prevention (DLP) controls
-
New/enhanced Separation of Duty controls
Figure 3: Comparison Reporting
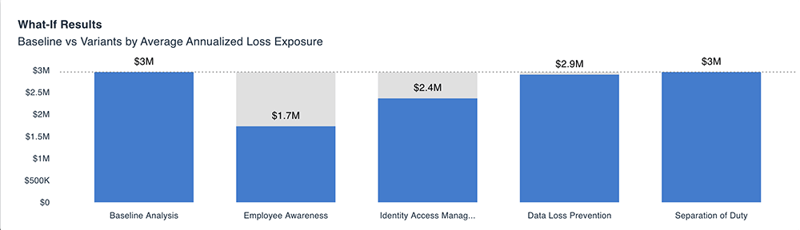
Using the RiskLens platform, we can run “What If” analyses to change one or more of your inputs and evaluate the resulting change in loss exposure, showing the effect of controls against the baseline in annualized loss exposure.
With quantitative analysis, we can get ahead of the threat actors, take reasonable cost-effective steps to keep BEC risk within tolerance levels, and balance spending across the security budget based on a solid understanding of cyber risk in financial terms.
Quantify Your Organization’s Email Risk Exposure
Quantifying your organization’s exposure to email risk, BEC and otherwise, is the best way to communicate it outside of your cybersecurity department; every decision maker in a business understands financial figures. Learn more about our platform here.
If you’re interested in specifics, contact us for more details.