 The U.S. federal government’s Cloud Smart policy directs agencies to prioritize cloud migration of IT assets, with an important caveat to follow the Federal CIO Council’s Application Rationalization Playbook and triage assets for migration on several factors including a risk assessment based on a “probability impact analyses.”
The U.S. federal government’s Cloud Smart policy directs agencies to prioritize cloud migration of IT assets, with an important caveat to follow the Federal CIO Council’s Application Rationalization Playbook and triage assets for migration on several factors including a risk assessment based on a “probability impact analyses.”
Forward-looking agencies are turning to RiskLens for just that service--the RiskLens SaaS platform, operating on the FAIR model for cyber risk quantification, offers guided data collection and automated analysis of probable loss exposure for IT assets, with reporting in dollar terms that decision-makers can readily understand.
Here’s a case study of how one federal agency used the RiskLens platform, with help from RiskLens consultants, to clarify decisions around its cloud migration project.
Erin Macuga is a RiskLens risk consultant specializing in government.
The Challenge
To evaluate the impact of migrating core applications to the cloud, the agency analyzed their primary concern: confidentiality of information. The following scenarios were analyzed both as they are today (on-premise), and the intended configurations in a cloud-hosted environment:
- External malicious actor compromising sensitive information in core applications
- Privileged insider accidentally compromising sensitive information in core applications
The Solution
Analyzing Current Risk Exposure On-Premise
The agency’s cloud migration team first needed to understand the risk associated with the current, on-premise version of the application. The RiskLens SaaS platform generated a set of guided “workshop” questions based on the scope of the analysis. Analysts then collected data to help define ranges for frequency and magnitude of a breach of the on-premise application.
Data-gathering involves looking at the six forms of loss in the FAIR model to help determine loss magnitude, for instance, loss of availability of the application, costs of responding to the data breach AND legal costs for damages from the breach. Analysts were able to use loss tables in the RiskLens platform to draw on loss data gathered from the agency, augmented with complementary data from industry sources. RiskLens consultants were able to customize the data for the specific needs of government, for instance putting dollar values on mission impact, loss of funding, management change or responding to GAO or Congressional investigations that might result from a breach.
The analysis also took into account the frequency of attacks the agency had experienced, as well as the strength of protective controls and other factors. Over the course of a week, the analysts were able to gather the data, while accounting for any uncertainty in data inputs by calibrated estimation to produce results in ranges.
The FAIR model is recognized as a resource for risk analysis and risk management in the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF), the basis of much of the security control baselines and risk management processes used by federal agencies.
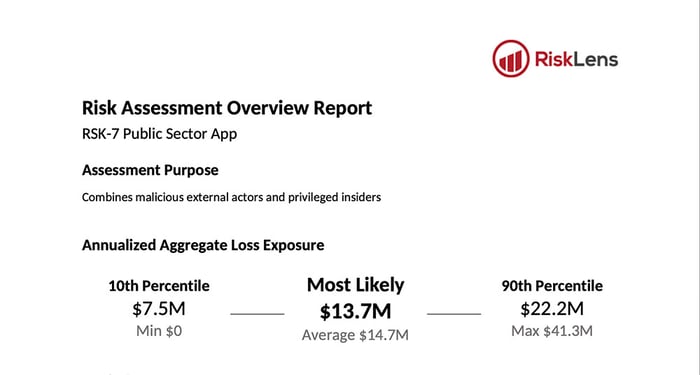
Through these data gathering sessions and after the input of the ranges into the platform, it was concluded that the on-premise application faced an approximate most likely aggregate annualized loss exposure (ALE) of $13.7M, if the application were to be breached by either external malicious actors or privileged insiders. (note: the number is fictitious, slightly changed from the original).
Analyzing Future Risk Exposure in the Cloud
Next, the analysis focused on the change in risk associated with migrating the on-premise application to the cloud, and used the RiskLens platform’s capability to conduct a future state analysis.
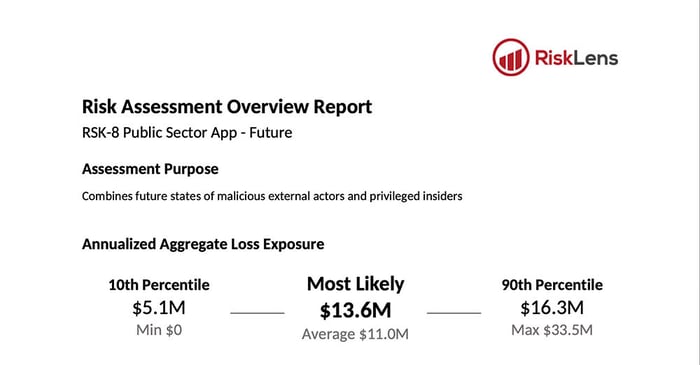
By isolating the area of the FAIR model most impacted by the migration, the analysts were able to assess the future state, considering the anticipated controls in place and control settings for the cloud solution. Having identified the changes to the original, current state analysis, they were able to rerun the analysis in less than a minute to understand the potential risk reduction for the cloud solution. Upon running the future state analysis, it was determined that while the most likely aggregate annualized loss exposure was not materially changed ($13.7M to $13.6M), there was an overall reduction in the average, as well as the 10th percentile, 90th percentile, and maximum if the application were migrated to the cloud (again, the numbers are slightly altered from the original).
These reports show a comparison of the current state analysis and the future state risk reduction for loss of confidentiality resulting from a data breach.
Key Benefits
 RiskLens enabled the analysts to quantify the loss exposure of a breach of the application. The inputs were accompanied with a rationale documenting how the data was gathered, which aided in any challenges to the ranges or why a data point may or may not have been included in the calculations.
RiskLens enabled the analysts to quantify the loss exposure of a breach of the application. The inputs were accompanied with a rationale documenting how the data was gathered, which aided in any challenges to the ranges or why a data point may or may not have been included in the calculations.
The key driver for the reduction in the average, 10th, 90th, and maximum was an impact to the overall susceptibility to attempts to breach the application, as a result of increased security measures in alignment with regulatory compliance such as FEDRAMP, as required for federal cloud hosted solutions. Additionally it was noted that the agency team responsible for the configuration of the security measures would be responsible in the event of a migration to the cloud were highly knowledgeable in cloud security and the controls of the application, to ensure proper configuration of the cloud storage. Due to the significant controls already implemented for the on-premise application, employing supplementary controls would have a slight, but tangible reduction in the agency’s vulnerability to a breach of sensitive information in the core application when migrated to the cloud.
In addition to the immediate value in discovering the probable loss exposure for each alternative course of action, the RiskLens analysis had another important value for the agency: demonstrating compliance with federal cybersecurity directives beyond Cloud Smart, such as
- The Federal Information Security Act (FISMA), related EOs and guidance form DHS explicitly require risk-based strategies and management processes for information security.
- Executive Order 13800 holds agency heads accountable for implementing risk management measures commensurate with the probability and magnitude of the harm resulting from cybersecurity events.
Federal officials: For more information on the benefits of quantitative cyber risk analytics to meet federal mandates, contact us.