 During turbulent economic times executives take a managed-risk approach to capitalization, revenue generation, and cost management. Almost all forms of risk are quantified into financial terms and can be managed effectively to help the business optimize under uncertain business conditions.
During turbulent economic times executives take a managed-risk approach to capitalization, revenue generation, and cost management. Almost all forms of risk are quantified into financial terms and can be managed effectively to help the business optimize under uncertain business conditions.
Notice I said “almost all forms of risk are quantified…” If risk quantification is prevalent in almost all forms of risk, how is it acceptable that cyber risk still be reported in qualitative terms? Is cyber risk that unimportant? I am sure that is not the case.
There are almost no corporate C-suite officers, risk and audit committees, or Board members that find it acceptable to operate oblivious to financial risk. Enterprise Risk Management does not report High/Med/Low or Red/Yellow/Green to stakeholders unless those qualitative designations are tied to financial loss exposure. Qualitative risk ratings are near meaningless when budgets are being cut and spending is being reprioritized.
What is more powerful? If we do not complete the encryption-at-rest project…
- “we have a high risk of a confidentiality breach” or
- “we have a $250M most likely loss exposure of a confidentiality breach this year”
Steve Tabacek is Cofounder & Managing Director, Customer Experience for RiskLens
Survey after survey reveal CEO’s have answered that cyber risk is a top organizational risk. Surprisingly, there are still large numbers of CISO’s that cannot comprehend or articulate how much risk they are managing in financial terms.
CEO: “How much cyber risk do we have?”
CISO: “I don’t know.”
The CISO is clearly operating oblivious to how business leaders make budget prioritizations and risk-based decisions. Boards, C-suite executives, and audit/risk committees should never find it acceptable when a CISO cannot express cybersecurity risk in financial terms.
A CISO should know the basic components that make up cybersecurity risk scenarios: 
- Assets: CISO’s should know the macro-level organizational, or micro-level department/business unit critical assets or “crown jewels” that drive the business.
- Controls: CISO’s commonly apply controls defined by NIST-CSF, NIST 800-53, ISO*, HITRUST, or other risk and control management frameworks to these assets.
- Threats: CISO’s also have access to resources constantly updating threats and threat types.
- Impact: CISO’s should never operate oblivious of probable impact.
Cybersecurity risk quantification frameworks and software have been in the marketplace for more than a decade. Factor Analysis of Information Risk (FAIR) is the risk quantification standard that has been used by government and corporations in every marketplace sector for the past decade. FAIR is a taxonomy of the factors that contribute to risk and how they affect each other. It is primarily used for establishing accurate probabilities for the frequency and magnitude of data loss events. Risk quantification software designed for cybersecurity and technology risk has advanced over the past decade enabling very efficient risk analysis, management, and reporting. CISO’s can no longer ignore current and best practices when people, process, and platforms are available enabling proper risk management.
An investment in cybersecurity and technology risk management will save money and reduce risk. It seems to be a no-brainer to spend 1-2% of a cybersecurity budget to ensure most effective and efficient allocation of the remaining 98-99%. How many CISO’s are allocated a cybersecurity budget of $10M, $20M, $40M, $80M, or more yet cannot articulate the ROI, effectiveness, or efficiency of their annual budget? This is no longer acceptable!
As a minimum, CISO’s should be able to communicate with Boards, risk committees, and C-suite executives the scenarios that could materially impact the organization. It should align with organizational risk appetite thresholds. 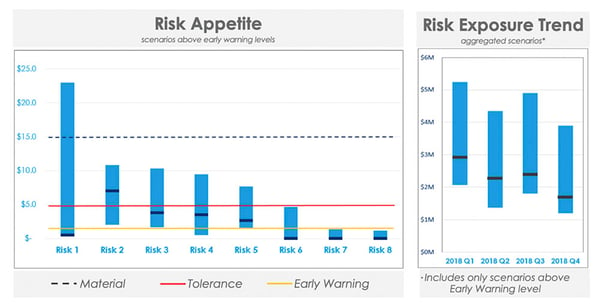
Furthermore, CISO’s should be able to answer the question: How are you reducing risk to an acceptable level? CISO’s should be able to demonstrate that they are evaluating mitigation options for top-risk scenarios, analyzing control deficiencies, and evaluating most efficient and effective mitigating controls such as the illustration below:
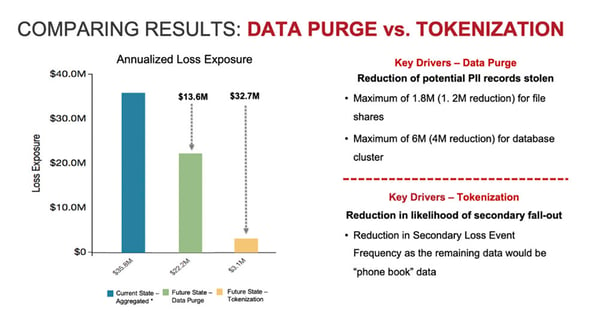
Especially in turbulent economic times, Boards and C-Suite executives should never accept a CISO operating with risk uncertainty. “I don’t know how much risk we have” is not an acceptable answer. Ultimately, CISO’s should be able to identify and communicate cyber risk in financial terms, then clearly demonstrate a reduction of risk over time or managing risk to an acceptable level.