One purportedly difficult thing to measure in cybersecurity is the impact of strategy. Ultimately, we should be able to tell executives how much risk they have before we execute our strategy, use it as the reason for the strategic decisions in the first place, and after they give us large sums of money, show them how risk has been reduced. This was the exact question that initiated the creation of what is now called the Factor Analysis of Information Risk (FAIR), the model trusted by 3,000+ leading thinkers across the Fortune 1,000 and that powers the RiskLens cyber risk quantification platform.
Since executives have to decide where their limited capital will be spent, it’s important to ensure they have the data necessary to make a well informed decision. Typically, it will not be someone in the security function who knows whether it’s more productive to spend $1 million on additional security, new product offerings, expanding into new geographical regions, new or expanded marketing campaigns, or acquiring other companies. Therefore, it is critical to the decision making process to place the security budget in the same terms as other risk based decisions.
At a high level, the process for setting cybersecurity strategy has to start with a view into what the current state of risk looks like. Then we assess what changes in control/risk posture would result from investments. Finally, we derive what a future state may look like after an investment.
Framing the Problem
 First, a quick primer on the nature of inherent risk versus present or current risk. The Cobit 5 for Risk standard acknowledges that the term inherent risk sometimes means “without controls” and sometimes means “present state” (p. 18). Many risk assessment methodologies have us analyze inherent risk (risk without any treatments) before applying controls to determine the current state (effectively deriving the current risk posture). This presumes two things (which are tenuous at best): 1) That an environment without controls can actually exist and 2) That we are unable to directly measure the current state of risk. The first assumption is fodder for an existential discussion. As for the second, it's actually quite straightforward to measure what is currently in place (it’s easier to take stock of the controls you have than pretending you have none). It's precisely this approach that will be used in the rest of this analysis.
First, a quick primer on the nature of inherent risk versus present or current risk. The Cobit 5 for Risk standard acknowledges that the term inherent risk sometimes means “without controls” and sometimes means “present state” (p. 18). Many risk assessment methodologies have us analyze inherent risk (risk without any treatments) before applying controls to determine the current state (effectively deriving the current risk posture). This presumes two things (which are tenuous at best): 1) That an environment without controls can actually exist and 2) That we are unable to directly measure the current state of risk. The first assumption is fodder for an existential discussion. As for the second, it's actually quite straightforward to measure what is currently in place (it’s easier to take stock of the controls you have than pretending you have none). It's precisely this approach that will be used in the rest of this analysis.
To begin, we will need to frame our problem as one of how to prioritize spending. Foundationally, all spending is done to address risk of some kind (such as in the economic sense of substituting capital for labor). We can think of statements of risk as statements of priorities; we are investing in this to avoid an otherwise undesirable outcome. For instance, it's pretty straightforward to talk about investing in controls to address explicit statements of risk: We invest in Data Loss Prevention (DLP) to address the risk associated with Data Loss and Theft.
But it's usually more difficult to find priorities for administrative things like investing in project management for security control implementation, or even basic things like hiring more resources to assess risk. But after careful review of these investments we can also tie them to statements of risk. One key way to do this is to use the approach from Douglas Hubbard’s How to Measure Anything around better defining our measurement questions using decomposition questions. Why are we looking to invest in expanded project management? Is it because we are unwilling to tolerate poorly managed projects? Why? Do we dislike budget overruns? Scope creep? Schedule overruns? Solutions that don’t meet our expectations? All of the above? Those all sound like measurable things. Now it's just a matter of using FAIR to estimate how often we experience those things (and associated costs), and how much less we may experience them after this investment (and how much less we are apt to lose).
Dr. Jack Freund is co-author of Measuring and Managing Information Risk: A FAIR Approach,
Let’s take another example: increased capacity/skills/coverage in a risk assessment program. This one may be a challenge as some may say that an assessment program won’t reduce risk, simply find out where more risk exists. However there are two places where this may be measured as a risk reduction effort. First, depending on your industry, there are regulations that require that you assess and manage risk. If you aren’t assessing it, that places you squarely in the crosshairs of being noncompliant with these regulations. That is a measurable: if you don’t expand your assessment program, how more often would you expect to experience regulator action? If so, how much would it cost?
But there is one other place to which we could map expanded risk assessment capabilities in your risk register: poorly managed risk. Typically it's good to keep a risk like this on the books as a way to manage problems you may encounter if you don’t run your risk assessment program in an appropriate fashion. For example, in a financial services company, this risk scenario may be represented in a register with a statement that says something to the effect of “Improperly managed risk leads to insufficient capital reserve allocations” (but really all companies maintain capital reserve allocations, just perhaps not at the behest of a regulatory body). Experiencing risk in excess of your reserves is a measurable thing that will allow you to show how expanded capabilities allow you to better manage that risk.
Building the Risk Assessment Framework
 Once we’ve clarified the measurement questions, next up is building the assessment framework through a series of risk statements. Essentially, for every item in your budget, you will need to align it with two things: 1) an item in the risk register and 2) a control. This will apply for all budgetary types such as “run,” “change,” or “project” budgetary requests. This allows us to identify a baseline for current state analyses and where changes to that may occur (through application of controls). If you don’t have a catalog of risks that can be used for this purpose, now is a good time to start building them. It's good practice to identify what risk that investment is working to combat. In so doing, it's wise to avoid defining risk as a series of “lack of” statements which typically just identify something as missing and fails to articulate the true underlying risk as a statement of loss. A missing control (lack of control) is not risky; risk is about what happens in spite of that or any other controls. The controls just factor into the frequency and/or magnitude of that risk scenario.
Once we’ve clarified the measurement questions, next up is building the assessment framework through a series of risk statements. Essentially, for every item in your budget, you will need to align it with two things: 1) an item in the risk register and 2) a control. This will apply for all budgetary types such as “run,” “change,” or “project” budgetary requests. This allows us to identify a baseline for current state analyses and where changes to that may occur (through application of controls). If you don’t have a catalog of risks that can be used for this purpose, now is a good time to start building them. It's good practice to identify what risk that investment is working to combat. In so doing, it's wise to avoid defining risk as a series of “lack of” statements which typically just identify something as missing and fails to articulate the true underlying risk as a statement of loss. A missing control (lack of control) is not risky; risk is about what happens in spite of that or any other controls. The controls just factor into the frequency and/or magnitude of that risk scenario.
Let’s talk about aligning your budgetary spend to controls for a minute. For the purposes of this exercise, we are working from a firm-wide, business unit, or legal entity perspective. As such, our controls need to be expressed at an equally aggregate manner as the risk statements to which they apply. For instance, if you’re using the early example of data loss and theft, the control category would be better as “access control” than as “password management.” Your mileage will vary, but mature organizations tend to have stratums of controls (and risk statements). The message here is simply guidance to help ensure that you summarize controls at the same level as the risks they help control.
So let’s assume the following simple set of risk statements:
- Internal Data Theft
- Internal Theft of Funds
- External Data Theft
- External Theft of Funds
- Supplier Theft/Loss of Data
Further, let’s also assume that you have budgetary items to address controls in the following areas that will combat Internal Data Theft:
- Monitoring
- User Access Management
- Data Loss Prevention
Justifying the Cybersecurity Budget Proposal
We can now prepare some basic risk-based support for our budgetary requests. Using FAIR, we can measure the current (inherent) state of risk, and then re-run the risk scenarios with each of the above control classes in place. It will be necessary for each project/run activity to be identified as having either a preventative or detective/responsive effect on risk. This will determine whether the budget item reduces loss events (preventative) or arrests them when they do occur (detective/responsive).
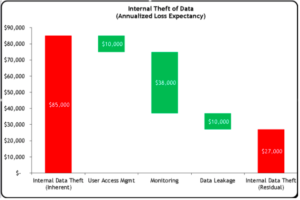
Once these calculations have been done, you can compile the results in a waterfall chart that illustrates where risk is currently, and why investing in your proposed budget can help to reduce risk in your organization: 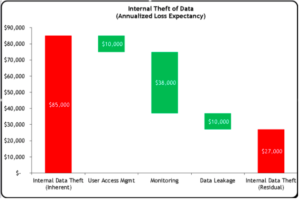
Cybersecurity Budget Risk Waterfall Chart
In the above figure, we can see in the far left what our current loss exposure is. We can also see how investing in each of the control groupings (User Access Management, Monitoring, and Data Leakage) will help in reducing that risk. The bar to the right illustrates what the risk posture will be after the investments for which you are asking.
This can be repeated for each risk statement that you have and for which you have project/budgetary items. Things can get tricky if you have one project that may affect different risk statements; you will need to determine if the control has different effects on each risk or if the same investment would affect all associated risk scenarios equally.
Charts like the one above allow for a rich conversation during budget season and invites executive management to the table in discussing their risk appetites and how they want to address it. It also serves as a tool to aid in absolving CISOs and their staff against adverse actions resulting from a decision to not invest in security. Which is to say that no organization has the money to invest in all the things they want. Budgeting is a hard, firm-wide exercise in setting priorities and strategies and those in the CISO’s organization don’t always have the same vantage point as the business units. However, it’s important that those who are ultimately making the investment decisions understand what they are choosing not to invest in, and how that can affect the organization. Exercises like the one above can aid in ensuring that your management is well informed before they make a decision about their cybersecurity investment.
If you are interested in enhancing your cybersecurity strategy with quantitative cyber risk data like the kind spelled out above, the Cyber Risk Quantification software from RiskLens can jump start your analysis. With purpose-built risk calculations and the flexibility to define bespoke control categories and investments tailored to your organization, this tool is an invaluable addition to any CISO’s toolbox.
Related: