Establishing a well-defined risk appetite has long been a moving target in cyber risk management. The conventional red-amber-green approach to cyber risk has influenced the treatment of risk appetite and led to some common pitfalls that become obvious when RiskLens consultants apply the principles of the FAIR model. Here are some of the problem areas we see:
- Risk appetite is often defined subjectively (e.g., what does “Moderately Low” mean?).
- The metrics are at best “loosely” associated with the appetite (e.g. there is no direct correlation of risk ratings to metrics).
- Organizations may be reluctant to state they are outside their appetite regardless of their metrics behavior/trending. As a result, the concept of having a risk appetite becomes difficult to implement in practice.
First, Define How You’ll Measure Risk Appetite
One of the factors emphasized by FAIR is the importance of leveraging consistency in terminology. This mindset can also be applied to risk appetite. It is important that key decision makers / stakeholders in the organization are aligned with how risk appetite should be defined (e.g., total of all losses, by category, single event). This also means that everyone involved in the risk management process should understand the decisions that will be made based on the defined risk appetite.
Once those factors are addressed, we are ready to move on to the establishment phase, which I describe in the three steps below. 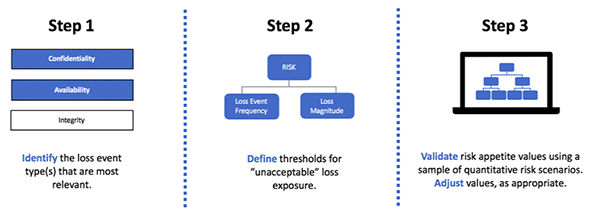
Set Your Risk Appetite in Three Steps
Step 1 – Identify the loss event type(s) that are most relevant
The thought process behind this first step is the notion that risk appetite may not represent a single value for cyber events. Rather, risk appetite may be defined differently for each (or at least derived differently). When working with our customers, we’ve recommended that they start the process by first focusing on the types of loss that are most relevant to their organization.
In the cybersecurity space, the three types of loss experienced are commonly refered to as the C-I-A triad (confidentiality, integrity, and availability). I recently worked with financial services company whose top five cyber risks all happened to be focused on confidentiality type events (e.g., data breaches). Therefore, we chose to start there.
Step 2 – Define thresholds for “unacceptable” loss exposure
Some organizations may not have an idea of what this “unacceptable” dollar value may be right off the cuff.
This is why it is important to establish leading questions to help drive the discussion around risk appetite. Rather than directly asking for risk appetite, develop a list of proxy questions to help drive the discussion such as:
- What does materiality look like from a financial reporting perspective?
- What is our current cyber insurance coverage?
- What are the largest security and availability events that have happened at our organization? What was the impact?
- What is the maximum duration of an outage for <insert critical system> that we are willing / able to withstand?
- What is the maximum number of confidential records we are willing to accept being breached?
If you are unable to establish an initial figure based in dollars and cents (which is the case with the last two questions listed above), you can leverage the power of the FAIR model to help arrive at a financial figure.
In keeping with the example from the financial institution referenced above, we posed the question of risk appetite in terms of records breached. By identifying a potential number of records breached that the organization would be unwilling to tolerate, we were able to plug in our estimates and run the analysis using RiskLens to ultimately derive a value for risk appetite in dollars and cents.
Tactically speaking, that meant performing a FAIR analysis assuming a data breach of 1M records (from the leading question) with an assumed loss event frequency of 1 event per year. From the output automatically generated by a Monte Carlo simulation performed with the RiskLens software, the financial figure representing the 90th percentile became the initial established risk appetite value.
Step 3 – Validate risk appetite value(s) using a sample of quantitative risk scenarios and obtain buy in
Once an initial risk appetite value has been established, it’s important to benchmark this figure against previously quantified FAIR risk analyses and obtain buy-in from key stakeholders. The figure below shows the results (using sanitized values) of the established risk appetite for confidentiality-related risk scenarios compared to the top five cyber risks identified by the financial institution:
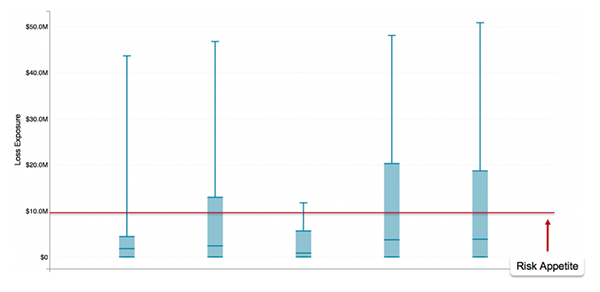
Each blue box indicates where the majority (80%) of the results of the simulated risk scenarios were contained (the whiskers represent the outliers). If we focus on the 80%, then the results indicated that three of top five risks had loss exposures that exceeded the organization's risk appetite. These results were socialized with the CISO, which helped to ensure that the established risk appetite value for confidentiality passed the smell test.
RiskLens can also be used to create trending reports that can monitor risk appetite against established cyber loss exposure values over time. When changes occur, such as the one circled in the graph below, management is faced with a key decision point on the appropriate action to take to ensure the loss exposure does not continue to trend upward. At this point, a decision on whether to invest in additional controls can be aided by performing a FAIR analysis to determine if the amount of the risk reduction in dollars and cents justifies the investment cost. 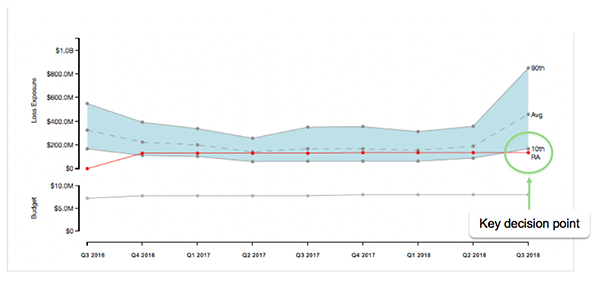
Learn more:
Data Breach Case Study: How RiskLens Modeled Risk Mitigation and ROI