Budget season is on and Information security executives could be playing their best negotiating hand in years, after a string of cyber attacks hit the bottom line hard in 2017. “Just don’t let us be another Equifax,” boards of directors are saying.
After 2017, chief financial officers have been confronted, if they weren’t already, with the reality that cyber risk is a financial risk that can cost millions in lost sales, productivity, stock value, fines and judgements. CFOs can’t afford to take the attitude that cybersecurity is just a technical cost center, too technical for them to understand, and exempt from financial risk analysis.
So what to make of the budget just lobbed in by the CISO?
What we should be asking and what we are getting
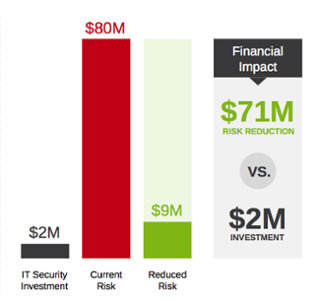 A CFO might start with these fundamental questions:
A CFO might start with these fundamental questions:
- How much risk—or loss exposure--do we have, in dollar terms?
- Are we spending too much or too little?
- Are we focusing on the things that can reduce risk the most?
- Should we drop some initiatives (for people or software) and double down on others?
- Are we adequately insured for cyber risk?
- For every new dollar you are asking for, how much will you reduce risk?
Sorry. If the CFO is talking to the typical infosecurity department, he/she shouldn’t expect direct answers.
According to a 2017 SANS Institute survey of cybersecurity officers, their top three success metrics in rank order were:
- “Improved compliance”
- “Reduction in attack surface”
- “Reduced breaches or compromises”
Not a financial metric to be seen—just benchmarks understood by others in the cybersecurity profession.
Take “compliance”. Translation: How many boxes have we checked on lists of best cybersecurity practices? How many ratings have we applied to maturity model spreadsheets? ( NIST CSF is currently one of such prevalent cybersecurity maturity models). Did we buy and implement “data loss prevention software”? Check.
By complying, organizations are assumed to have less risk. But control frameworks and maturity models don’t measure risk or show an ROI for implementing more or less of one best practice vs. another, on one set of IT assets vs. another.
That doesn’t stop the typical CISO for asking for more money for more controls to check more boxes. Need a clinching argument? “You don’t want to be another Equifax, do you?”
Articulating cyber risk in monetary terms
There is a better way to budget than one based on fear, box-checking or Trust a Techie.
Standard methodologies to assess risk in financial terms such as Factor Analysis of Information Risk (FAIR) have emerged in recent years. FAIR, an international standard by The Open Group, helps articulate cyber risk as probable annual loss exposure, by taking into account all the factors that make up risk, including threat event frequency, threat capabilities, state of controls, primary and secondary forms of losses and leveraging the power of math (Monte Carlo simulations), as for any other form of enterprise risk. 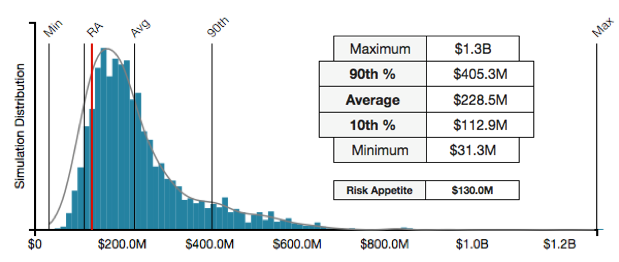 Commercial software such as RiskLens allows large organizations to conduct such quantitative risk analyses at scale, and include advanced capabilities such as what-if and sensitivity analyses. The result is generated in monetary values that enable cost-benefit analysis, where the costs of various security initiatives can be compared to possible risk reductions. This is allowing many organizations across industries as varied as retail, banking, insurance, healthcare, manufacturing and technology to optimize their cybersecurity budgets and prioritize the projects that reduce risk the most.
Commercial software such as RiskLens allows large organizations to conduct such quantitative risk analyses at scale, and include advanced capabilities such as what-if and sensitivity analyses. The result is generated in monetary values that enable cost-benefit analysis, where the costs of various security initiatives can be compared to possible risk reductions. This is allowing many organizations across industries as varied as retail, banking, insurance, healthcare, manufacturing and technology to optimize their cybersecurity budgets and prioritize the projects that reduce risk the most.
The dark ages, when budgets are determined based on technical best practices alone, subjective risk assessments or Fear-Uncertainty-Doubt are over. Now CFOs can – and should – demand financial based reporting on cybersecurity risk.
Learn more about how to manage cybersecurity from the financial perspective. Contact us for a free consultation.