In a recent blog post by Jack Jones on Dark Reading, the creator of the FAIR model for cyber risk quantification analysis writes that “as a profession, we've been saying for a long time that we need to speak the language of business in order to get and maintain the support we need to be effective.”
Yet so many well meaning CISOs keep making “executive stakeholders…eyes glaze over when we talk about vulnerabilities and threat vectors,” as Jack writes. Surveys of board directors consistently rate CISOs at the bottom for presentation skills. In one survey, the Cyber Balance Sheet, CISOs actually listed as one of their top values to the organization “business enablement”—while directors in the same survey listed that value for CISOs at the bottom. Directors placed data and brand protection at the top of their list, the opposite of the CISO choices.
What we’ve got here, for many CISOs, is not just failure to communicate but a lack of situational awareness as to how they line up with the rest of the business.
It’s Time for the Business-Aligned CISO
Times have changed. After more than a decade of each new year being the "Year of the Breach," an endless stream of intellectual property theft, ransomware-induced business interruptions, and intensified scrutiny from regulators (see the new GDPR rules or the SEC guidance on cybersecurity disclosure), the conclusion has finally been drawn that cyber risk = business risk in the eyes of the board and senior management.
Despite the desire to drive better alignment to the business, many CISOs have struggled to change with the times. They still see cybersecurity as an IT problem, too technical to explain to the muggles in the executive suites. Even if they take a broader view, they lack the mental models or analytical tools to communicate in terms the rest of the business understands. So, they resort to arranging cyber risks on a heat map based, in many cases, on gut feelings or pointing to progress meeting best-practices checklists like the NIST CSF based on the assumption that more boxes checked means less risk.
Ask them to align with the common practices of enterprise risk management—such as showing value at risk or return on investment for mitigation – and they’re not sure how to do it. They can’t answer the basic, and now urgent questions like “How much cyber risk do we have?” or “What are our top risks?”
Businesses aren't going to wait for this visibility any longer.
“We need to mature and start understanding that our jobs are to enable the business to make more money. We don’t have jobs to make the business secure. Everything we do should align to our corporate goals. The problem is so often we don’t understand the business well enough to do our real jobs.” --Matt Martin, Vice President, Technology Risk, at LPL Financial and FAIR practitioner.
The FAIR Model for Risk Quantification – How CISOs Align with the Business
Risk in my mind is the bridge that connects the business world to the technical world of security controls.
--Omar Khawaja, CISO at Highmark Health and FAIR practitioner
FAIR (that’s Factor Analysis of Information Risk) is a way to think through cyber risk and translate it into terms that the business demands, namely loss-causing events—because ultimately, it’s losses that concern the business not vulnerabilities or threats. ( See the FAIR model here.) Secondly, FAIR analysis is a way to value cyber risk in financial terms (or cyber risk quantification), putting cybersecurity investment decisions on a par with any other enterprise risk decisions
In fact, just to follow the FAIR methodology is to accomplish alignment with the business.
Phase one in a FAIR analysis is to scope the problem and gather data. Analysts talk to business unit owners and subject matter experts to gain a full understanding of the products, processes and assets that “enable the business to make money,” as Matt Martin says (or lose it), with the goal of defining a risk to analyze that will support a business decision. 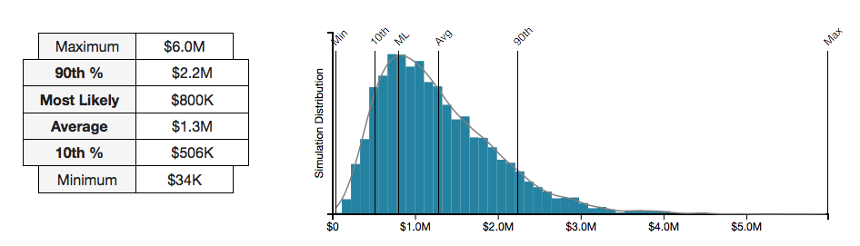
With help from these experts, analysts define the type of loss that might occur (Confidentiality, Integrity, Availability), the likely loss event (ransomware attack by cybercriminals, etc.), the effectiveness of controls, and the value of likely losses based on company and industry data (cost of loss sales due to unavailability of systems, etc.).
Phase two is to run the risk quantification analysis. The RiskLens application automates the FAIR model and runs the data through a Monte Carlo engine to return a range of probable losses in dollars. A range (including Most Likely, 90 th Percentile, Maximum, etc.) enables decision makers to compare results against risk appetite, as in other enterprise risk analyses. With the RiskLens Sensitivity Analysis function, the analysis can be tweaked to game out the effects on loss exposure of adding or subtracting different controls, useful for targeting spend on infosecurity.
From the sources of the data, through the process of the analysis, to the results in dollars, the FAIR approach is transparent, understandable and defensible. It makes for some cool charts, too – but with a deeper message: This is what a business-aligned CISO looks like.
Related:
Gartner Names Risk Quantification a Critical Capability of Integrated Risk Management