 When a cool new trend emerges in the tech world, we inevitably see marketing professionals at vendor organizations trying to capitalize on it. Suddenly, a flurry of companies change their messaging and position their products as the best way to meet those new trends.
When a cool new trend emerges in the tech world, we inevitably see marketing professionals at vendor organizations trying to capitalize on it. Suddenly, a flurry of companies change their messaging and position their products as the best way to meet those new trends.
I have to admit: It's tough to resist. When customers are asking for that new 'thing', it's very tempting to align one's solution to requests that have demand and funding.
This is happening today for 'cyber risk quantification'. As company boards, governments and regulators are asking for cyber risk to be communicated in the language of the business, the term 'cyber risk quantification' is becoming more prevalent in conversations between buyers and sellers.
As in every nascent market niche, a new term has no standard definition, and every vendor will put its own spin on the concept. This ultimately leads to confusion in the marketplace where the same term is used for many different things. Over time, customer requirements become more precise and vendors can be classified and differentiated by more distinct (and better named) market segments.
As the pioneers and leading providers of 'cyber risk quantification' we - at RiskLens - have been asked what the term means countless times. In this post, we'll get to the core of those questions by analyzing what each term means.
Watch a short video explaining the FAIR model and RiskLens
What is 'Cyber Risk'?
It may come as a surprise, but a standard risk taxonomy and risk quantification model already exists in the cybersecurity risk realm. The Open Group, the global standards consortium based in San Francisco, settled on the matter after years of model research and validation by selecting FAIR as: 1) its standard information risk taxonomy and 2) its standard methodology for analyzing information risk.
The Open Group is supported by close to 600 member organizations including many leading technology vendors, the world's largest enterprises, and government organizations and universities. They select technical standards that help solve business problems. While FAIR has initially been used to scope and analyze information risk scenarios, the standard is agnostic and can also be applied to operational risk.
Recognition for FAIR
- The National Institute of Standards and Technology (NIST) recognizes FAIR as an "Informative Reference" for risk assessment and risk management in its Cybersecurity Framework (NIST CSF), the most widely used framework in the US.
- The non-profit FAIR Institute counts more than 10,000 members worldwide, with representation from about 30% of Fortune 1000 companies.
- The Wall St. Journal's Cybersecurity Pro Newsletter reports that "FAIR is gaining traction, especially among large corporations that already have experience with cyber risk analysis.”
According to FAIR, risk is defined as "the probable frequency and probable magnitude of future loss," associated with a specific event. The way in which possible losses materialize must be articulated in risk scenarios that describe the action of a threat onto an asset of value and the resulting effect. In this picture, risk is synonymous with loss exposure.
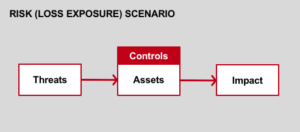
So, to accurately describe a risk scenario, one needs to define the asset of value, the threat, the threat effect and the resulting impact. If one of those elements is missing, we can't properly talk about risk.
Unfortunately, this is where many of the problems in our industry start: with erroneous definitions. Customers and vendors alike use the term 'risk' liberally to describe things that sound scary and use it interchangeably to talk about threats, control deficiencies and forms of loss. Those are all factors that can contribute to risk but do not constitute risk in isolation. In a cyber context, risk is NOT:
- A deficiency in an organization’s cybersecurity controls
- A threat actor – hackers, larcenous employees, the North Korean army
- A form of loss - productivity loss, reputational loss, privacy liability
Using an accurate and consistent taxonomy when speaking about risk, as in FAIR, can make an immediate positive impact to organizations that otherwise end up chasing ghosts and wasting time and resources, such as fixing vulnerabilities that do not matter because there are no significant threats or assets of value associated with them.
What does 'Quantification' mean?
Per the Oxford Dictionary, quantification means "the expression or measurement of the quantity of something." The ideas that gave birth to FAIR were prompted by simple questions related to this definition in a board meeting when a then-CISO (Jack Jones, the author of FAIR) was asked: "How much cyber risk do we have?" and "If we approve your cybersecurity budget, by how much will you reduce it?"
The FAIR model helps answer these questions by decomposing risk into discrete factors that can be quantified. At the highest level of abstraction, risk is the result of the probable frequency and probable magnitude of future loss. Frequency is typically calculated by estimating the probable number of loss events in a defined time interval, while losses in a business context are typically expressed in financial terms. The combination of the two factors, within specific risk scenarios, results in an expression of risk or loss exposure in financial terms.
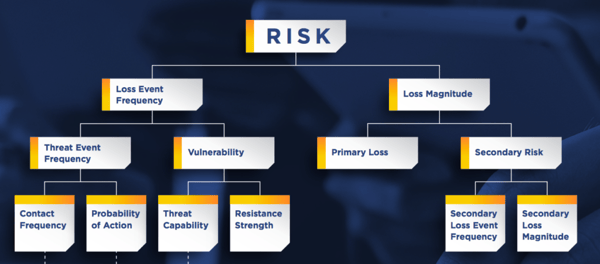
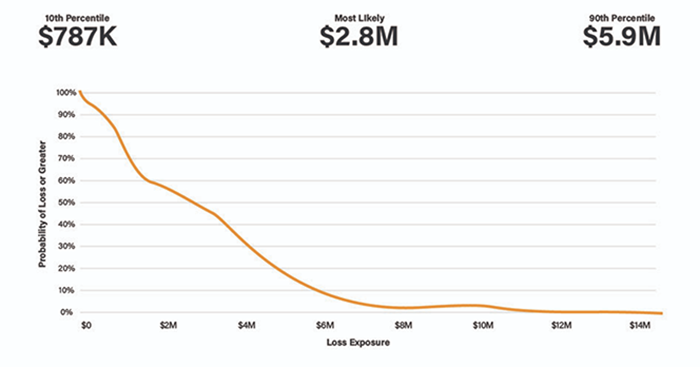
Since you want to take into account the inevitable variance that exists in real life, inputs for each factor of risk are ranges (with a min and a max) and Monte Carlo simulations can be used to calculate the resulting risk. The resulting risk measurement is a curve that shows the probability of various amounts of losses on a continuum in a given timeframe. The horizontal axis will display the probable amount of losses, while the vertical axis indicates the percentage of scenarios (ex. out of 10k simulations) that would result in the various amounts of losses.
How does this help us in managing risk?
FAIR defines risk management as "the combination of personnel, policies, processes and technologies that enable an organization to cost-effectively achieve and maintain an acceptable level of loss exposure." It becomes clear then that the only models that help achieve true risk management quantify risk in financial terms. In this context, risk management professionals can evaluate which risk mitigations are most effective in reducing risk and can present options to management, based on cost/benefit analysis. Executive management and the board can better fulfill their governance roles by making well-informed decisions about risk where options and alternatives are expressed in the familiar language of dollars and cents (or Euros, Yen, GBP, etc.).
Traditional risk management approaches that rely on qualitative measurements such as High-Medium-Low or ordinal scales 1-10, besides being inherently flawed, fail to quantify risk in ways that makes sense to the business and certainly do not enable cost-effective decision making. After all, how much should you spend to mitigate a 'Medium' risk? What's the ROI if you reduce a risk from a 5 to a 2? It feels embarrassing to even ask the question, yet this is where we stood as a profession until recently.
Making sense of the confusion with 3 key questions
Having established a set of foundational definitions thanks to FAIR, you can now orient yourself in the marketplace where many vendors claim to be offering cyber risk quantification solutions. Ask yourself the following questions:
1. What do they mean when they talk about risk?
Are they just talking loosely about it, but only offering a score that measures application vulnerabilities and control deficiencies? Are they attempting to measure the level of threat activity? Or are they measuring the maturity of their risk management practices as in NIST CSF (which recommends the use of FAIR in risk assessment and risk management)?
2. What is the underlying model?
Are they using a standard and validated quantification model such as FAIR, or are they relying on some kind of proprietary model powered by a black-box engine? What assurance can you have in the validity and accuracy of those models? Are they quantifying risk in financial terms or relying on a score?
3. What is the objective of their analysis?
Are these vendors helping you manage the economics of cyber risk, helping prioritize what matters most from the business perspective, conducting cost-benefit analysis? Or are they helping security operations sort through vulnerabilities and threats, without a clear tie to the business impact? Are they targeting security operations or risk management?
These are fundamental questions that will help you separate vendors from one another. Just because third-party risk management, threat intelligence or vulnerability assessment vendors provide a "risk score" does not necessarily mean that you will be able to make sense of what matters the most from the business perspective. Some of these solutions are attractive because they promise a quick and seamless implementation but you may still end up in the dark when it comes to understanding risk as you get volumes of alerts with little or no business context. Learn more: Read the Ultimate Buyers Guide to Understanding Cyber Risk Quantification by Jack Jones, creator of the FAIR model.
RiskLens is the only enterprise software platform purpose built on FAIR
Be wary of vendors that slap a “cyber risk quantification” label on current wares because they see a market trend emerging. Get a true cyber risk quantification solution. RiskLens is happy to partner with your company to help you build your quantitative cyber risk management program. Together we can help the industry drive the change that’s needed and enable cost-effective decision making. Contact us.