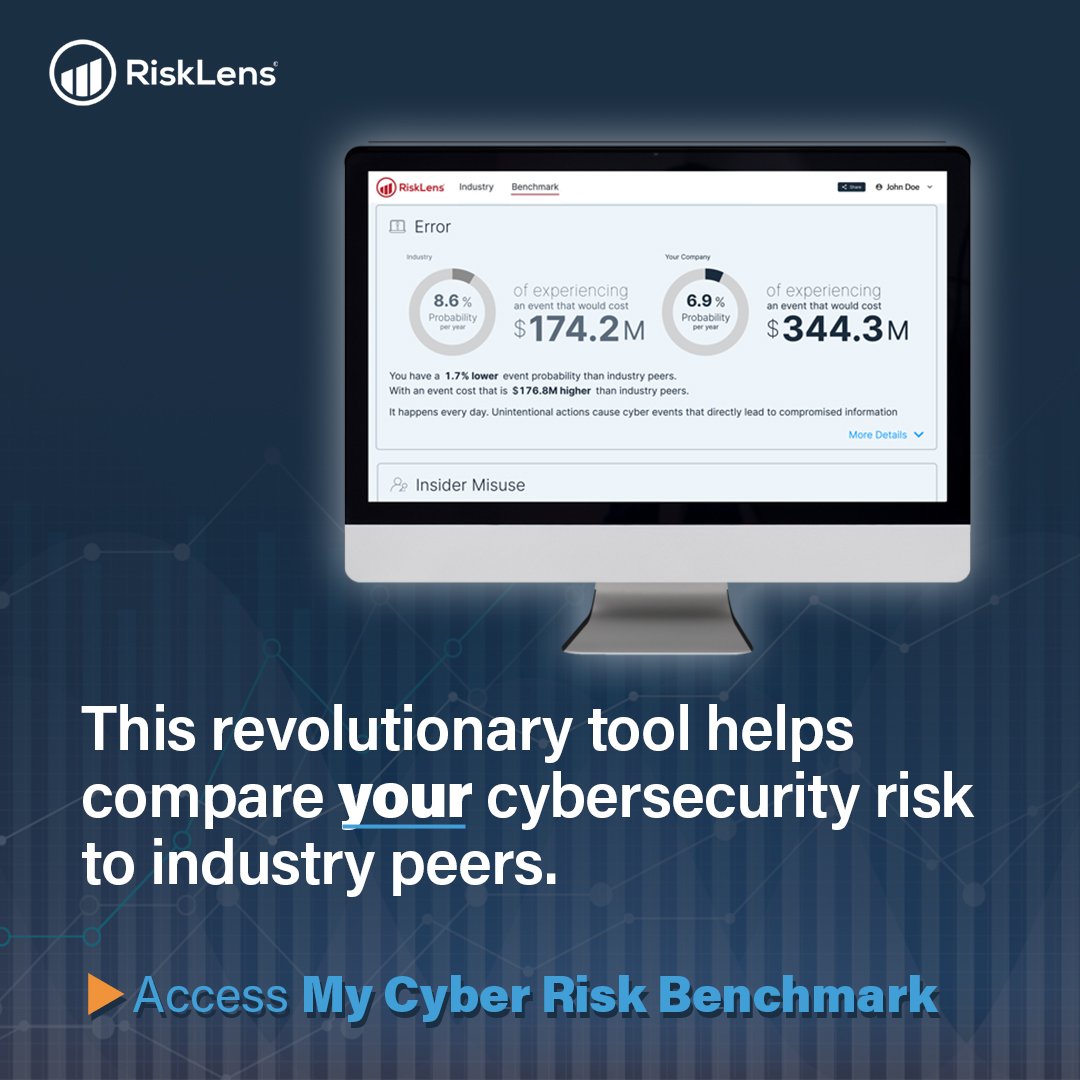
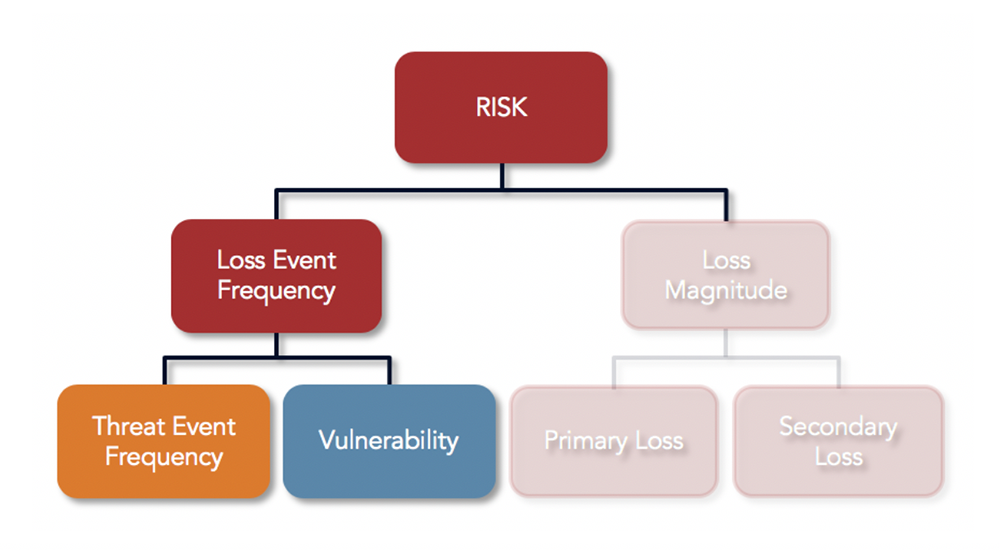
I was first introduced to the concept of cyber risk quantification when I began working with Factor Analysis of Information Risk or the FAIR Model (see a diagram of the model here). With this model, an analyst can estimate cyber risk in financial terms (i.e., dollars and cents). In FAIR-based risk analysis, measurement of risk doesn’t result in a “score” or a “rating” but in a range of monetary loss the organization might face from a given scenario over a given timeframe, typically the next year. In the FAIR definition:
Risk = Probable Frequency and Probable Magnitude of Future Loss
Risk at its highest level in the model is comprised of two variables, Loss Event Frequency and Loss Magnitude. If we are able to accurately estimate how many times a loss event will occur and how much we can expect to lose each time, we can derive how much risk we have from the scenario being analyzed.
The model further breaks down these two factors into subcomponents that can be estimated based on information collected from subject matter experts or industry data, then built back up into accurate, overall estimates of Frequency and Magnitude, with Magnitude expressed in terms of dollars and cents.
 Rachel Slabotsky, Director, Professional Services, explains the FAIR model that makes cyber risk quantification on the RiskLens platform accurate, reliable and defensible.
Rachel Slabotsky, Director, Professional Services, explains the FAIR model that makes cyber risk quantification on the RiskLens platform accurate, reliable and defensible.
Applying FAIR to a Cyber Risk Scenario
Let’s walk through an example of how a cyber risk scenario can be decomposed using FAIR:
Scenario: Analyze the amount of risk associated with cybercriminals breaching personally identifiable information (PII) from a “crown jewel” database
The FAIR Model helps us decompose the question “How much risk do we face from this scenario? Defining a scenario requires:
- An asset: crown jewel database containing PII
- A threat: cybercriminals
- An effect: confidentiality loss
Without these three components clearly identified, cyber risk cannot be accurately measured.
Frequency
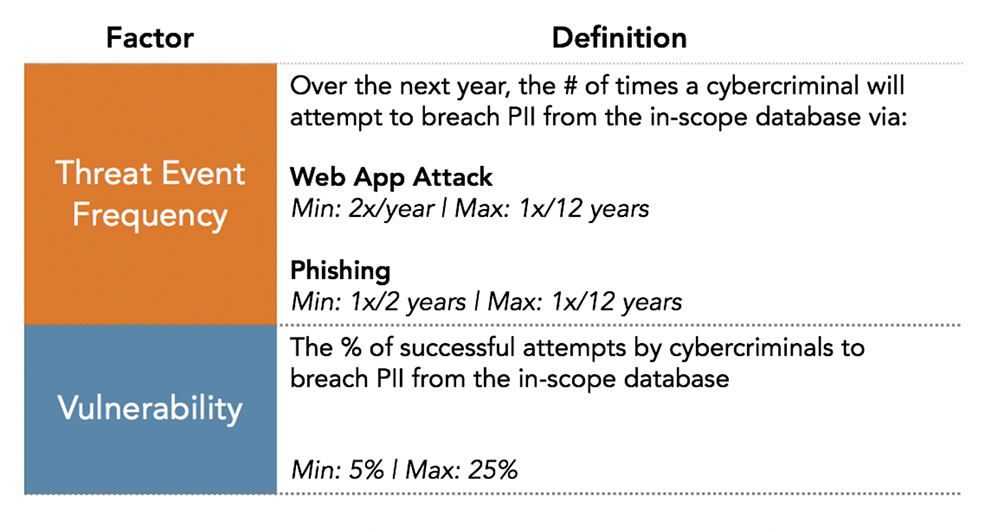
In this example, industry data and the best internal data available from subject matter experts was obtained at the Threat Event Frequency and Vulnerability factors of the model. Data was gathered to estimate the minimum, maximum and most likely values as well as the analyst’s degree of confidence in the most likely value (note: only the minimum and maximum values are pictured for illustrative purposes).
Providing a range of inputs allows the analyst to account for the uncertainty of the data – which helps to address a limitation of traditional heat maps, where there is a tendency to gravitate toward the worse-case scenario since analysts are forced to choose a specific value (e.g., red, yellow, green). Values for the resulting Loss Event Frequency (i.e., the estimated number of times over the next year that cybercriminals successfully breach PII in the crown jewel database) are generated by running a series of Monte Carlo simulations to capture probabilistic outcomes based on the data provided.
Magnitude
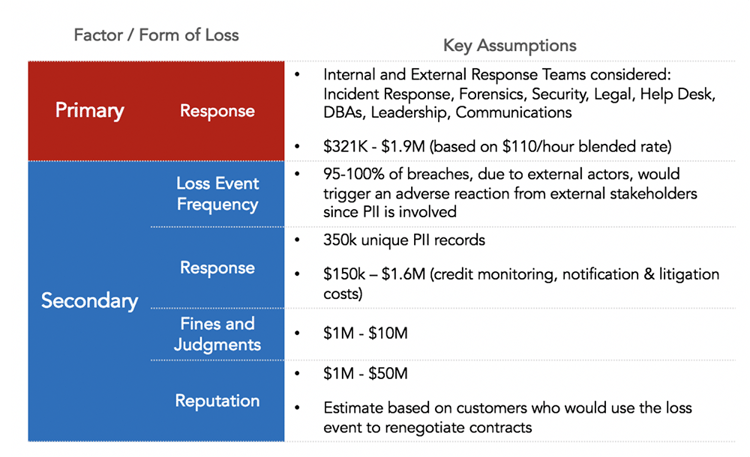
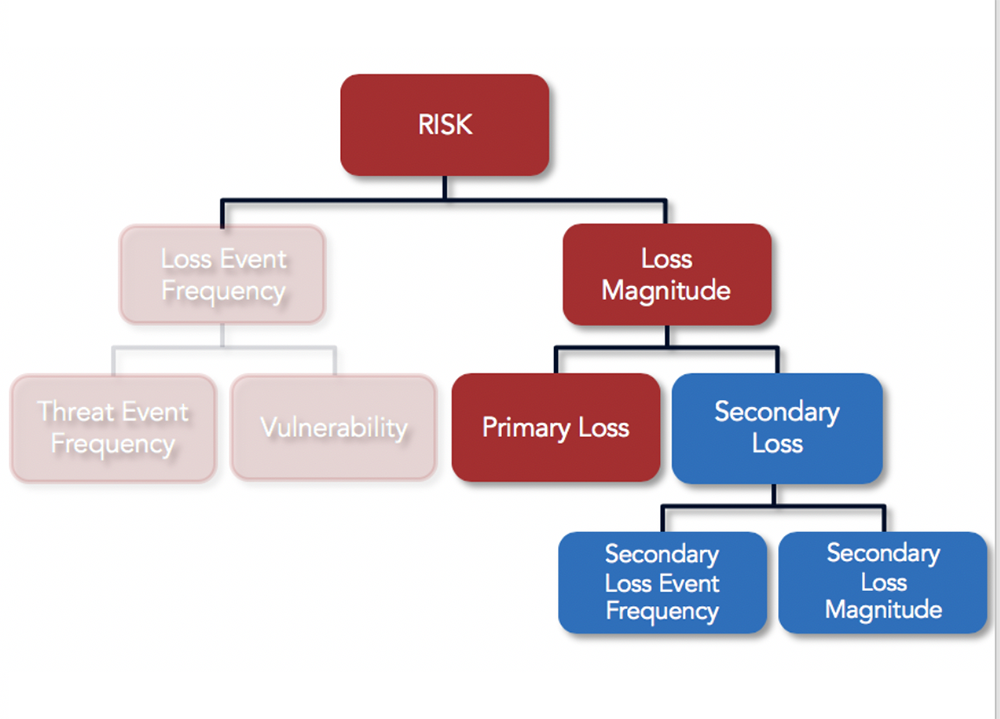
Data gathered on the Magnitude side of the model is used to determine the amount of monetary loss the organization will experience directly each time a cybercriminal is able to successfully breach PII from the crown jewel database (Primary Loss) and the additional amount of loss due to the reactions of external stakeholders from the breach (Secondary Loss). Because the reactions from external stakeholders may not be guaranteed, the model accounts for this by estimating how likely the organization is to experience further loss from stakeholders (Secondary Loss Event Frequency).
Using the FAIR Model, we are able to take the estimates above for each of the factors of risk so that we can derive estimates of annualized loss exposure by running thousands of Monte Carlo simulations on the RiskLens platform. Below is an example of the resulting probabilistic statements of how much loss the organization is likely to experience, as illustrated by a loss exceedance curve. This curve shows us, for instance, that it is most likely that the organization will lose $10 million or more from this scenario over the next year. The chart below that shows the results for loss exposure at the 10th and 90th percentiles and the average (or most likely).
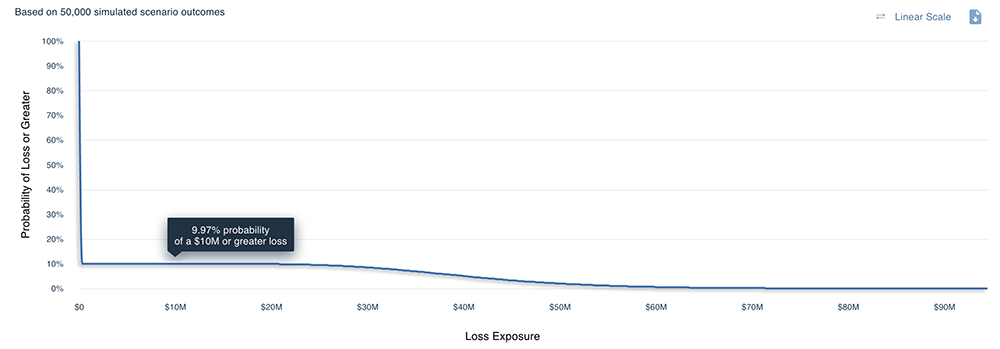
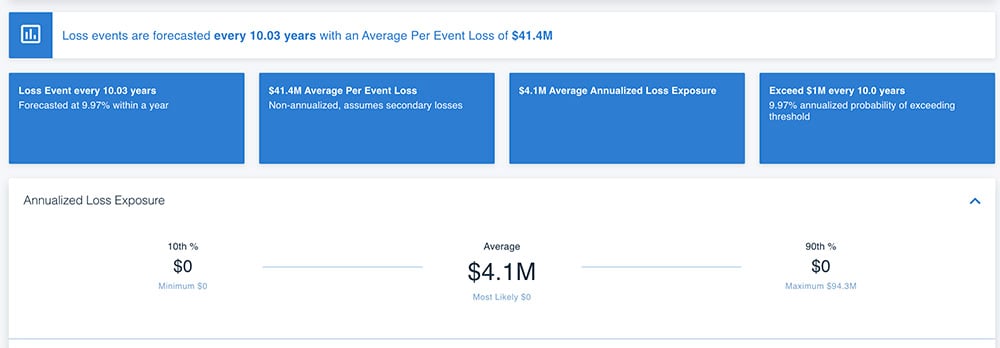
Analysis results from the RiskLens platform
Instead of mental models that vary by analyst, leveraging the FAIR Model allows analysts to produce consistent, repeatable results that are defined in business terms. When CISOs/CIOs begin speaking the same language as executives, line-of-business managers, and other stakeholders they can begin to answer questions such as:
- What are the organization’s top cyber risks and how much exposure do they represent?
- Which cyber risk management investments matter most?
- Are we investing enough (or too much) in cyber risk management?
- What is the return on investment for risk reduction for any mitigation
- What is our loss exposure compared to our risk appetite?
RiskLens Automates FAIR Cyber Risk Quantitative Analysis
The RiskLens enterprise platform speeds analysis with these features and functions:
- Guided risk assessment workflow based on FAIR.
- Pre-packaged risk scenarios and benchmark data for fast risk analysis on the most common use cases: reporting on top risks, emerging threats, security investment prioritization, and more.
- Embedded risk quantification engine for Monte Carlo simulations.
- Portfolio Management to track and manage risk in nearly limitless variations – by business unit or entire enterprise, geography, revenue stream, type of cyber attack and more, continuously updated.
- Reporting on risk in financial terms easy to understand for non-technical business leaders.