“Measurements will be critical to ensure that cybersecurity receives proper consideration in a larger enterprise risk management discussion.” said Matt Barrett, NIST’s program manager for the Cybersecurity Framework.
The introduction of measurement concepts within the draft NIST 1.1 Cybersecurity framework is a nod towards quantifying cyber risk. However, let's not get too excited yet. The maturity framework itself still relies on the existing 1-4 qualitative scales. What is more interesting is the conversation within the framework of suggested methods of measurement within the implementation tiers.
Mapping Common KPI/KRI Metrics
One proposed measurement method is mapping common KPI/KRI metrics to the various factors within an implementation tier. An example from the draft framework:
"For instance, the outcome of the Protect Function is to “develop and implement the appropriate safeguards to ensure delivery...” A Senior executive held accountable to this outcome might be measured using a lagging metric of percentage uptime of system(s) (i.e. ensuring delivery)."
While this is a step in a positive direction, it is my belief that the actual value and the ability to make informed business decisions from this tracking/trending will be quite limited. Likely we will see dashboards with measurements like this: 
Measurement Models To Complement NIST CSF
The conversation I would like to start is how Factor Analysis of Information Risk (FAIR) can be an effective method of measurement to complement the NIST CSF framework.
How can it help? Let's revisit the aforementioned example on system uptime percentage mentioned within the NIST draft.
We find that management needs to know two critical pieces of information from a risk perspective:
- What is the frequency by which we suffer outages on our key systems?
- When those outages occur, what is the estimated cost (in dollars, not qualitative scales)?
When those two are combined, we are able to, in a single "measure," speak to the risk in financial terms associated with uptime of key systems to management. For those that have performed a FAIR analysis with a solution like RiskLens, this is very straightforward. 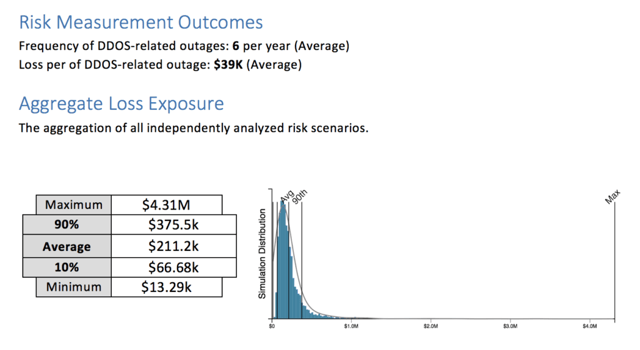
But remember... these results only inform the current state of risk exposure. Management should also be informed on the cost effectiveness of proposed controls/processes to reduce that exposure. This is when risk analysis provides strategic value and drives decisions or actions.
Using the above mentioned current state FAIR analysis, within the RiskLens platform, we can create an iteration and make forecasted estimations to the FAIR factors associated with the proposed changes and re-run the analysis. We are now able to communicate risk reduction opportunities as part of cost/benefit analyses. 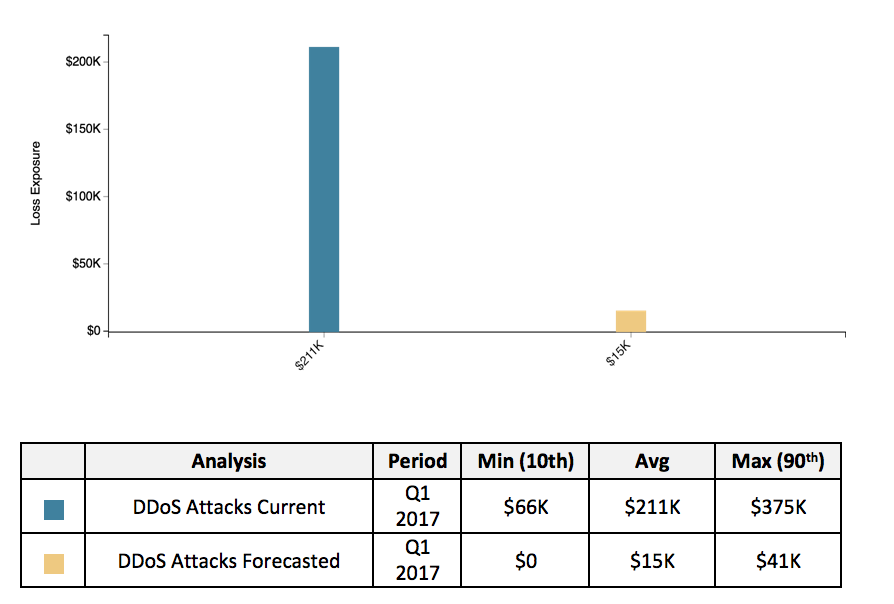
In conclusion, the draft NIST CSF 1.1 update is highlighting that maturity models alone aren't enough and that measurement on cybersecurity is critical to ensure it is included within the larger enterprise risk management discussion. While the draft framework started the discussion on measurement... we at RiskLens have been doing it effectively for years. Let us show you the way forward.