
It’s a safe bet that across the world, boards of directors have asked cybersecurity management teams this week: “Are we running infected SolarWinds networking monitoring software? And if we are - what’s our risk?”
With 18,000 clients having downloaded malware hidden in an update, the answer to the first board question for many major enterprises and government agencies will be “yes”.
The complete answer to question two at affected organizations won’t be known until lengthy forensic work is completed. But RiskLens clients can respond quickly with a report showing a range of probable losses in dollars, just what decision-makers look for in a time of crisis – or to plan defense against a future sophisticated advanced persistent threat (APT) assault on their network.
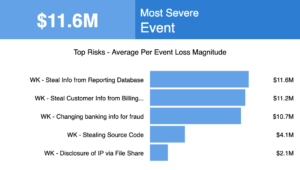
The RiskLens platform runs quantitative cyber risk analysis based on Factor Analysis of Information Risk (FAIR™), the international standard for risk quantification. The Rapid Risk Assessment capability of the platform can analyze in minutes risk scenarios, each describing a different loss event, and generate a prioritized list of risks ready for board review.
The SolarWinds attack, from a FAIR analysis point of view
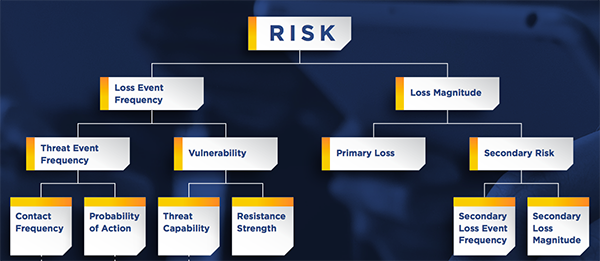
FAIR analysis achieves its accurate, quantifiable results by tightly focusing on risk scenarios defined as a threat acting on an asset to produce a loss. The result is an analysis of risk (or a loss event) based on the probable frequency of event and probable magnitude of loss (see this visual representation of the FAIR standard for analysis).
The SolarWinds hack suggests plenty of risk scenarios to analyze.
(One Scenario = Threat >> Asset >> Loss Effect)
Threat: A sophisticated nation state actor
- Method: Inserted malicious code empowering the attackers to pass as privileged insiders with wide permissions across networks, including the ability to create backdoors to admit more malware and communicate to controlling servers.
Assets: Many. The attackers might go after databases, industrial control systems, customer-facing web applications, email…
Loss Effects: Across the C-I-A spectrum, potentially:
- Confidential information from contracts, financial reports, internal memos, customer data…
- Integrity compromises such as corrupting, wiping or locking up data, ransomware-style
- Availability consequences from disrupted operations – starting with unplugging the SolarWinds applications up to rebuilding entire systems to assure knocking out the malware.
How FAIR analysis with the RiskLens platform turns risk scenarios into quantifiable, useful decision support
The RiskLens/FAIR platform and process guides you with a simple question/answer format through every step to gathering the data (within the organization and with industry-standard data) and crunching the numbers to produce an analysis.

Data Helpers
Much of the detailed information you collect internally gets recorded in Data Helpers as factlets to be plugged into analysis (for instance, what percentage of cyber intrusions would be caught by your SOC team).
Loss Tables
FAIR analysis covers six forms of loss (see the list to the right) and it’s not hard to match them with our anticipated SolarWinds loss effects. The platform allows you to build out consistent, reusable loss tables to aid in capturing the expenses associated with various forms of loss. These tables are then automatically leveraged in relevant analyses--saving you time and effort.
Asset Manager
The catalogue of your assets that can include the type and value of the data they contain and the strength of the controls protecting them.
Risk Scenarios
Creating a risk scenario on the platform then is a matter of following the guided workflow and automatically pulling in the detailed information captured in Loss Tables, Data Helpers and Asset Manager. The risk scenarios themselves are stored on the platform for easy access.
Run the Analysis and Report
We’re back where we started, handing off our report to the board. Next steps could be running detailed reports on the top risks, with more data for more accuracy, then running Risk Treatment Analysis reporting to understand the cost/benefit implications of adding controls or changing processes to prevent a future SolarWinds-style incident.

Going forward…
While it’s early to discuss lessons learned with any confidence, some general points are pretty clear, coming out of the SolarWinds incident:
- Cyber risk = business risk. It’s hard to think of more existential threat than knocking out an organization’s networks, as the attackers certainly could have done--and we don’t know yet the damage done by exfiltrating data or intellectual property, for instance. Boards and everyone down and across the chain of command need to coordinate on cybersecurity. Having a common, financial language to understand risk is a must.
- Value community. The SolarWinds attack was made public by private enterprises—FireEye, Microsoft and others—openly sharing knowledge for the common good. FAIR practitioners have the FAIR Institute or the RiskLens user community for sharing best practices, and there are many more community and educational groups.
- Know your key risks, plan for risk treatment. New information that emerges about SolarWinds or other advanced threats give new indications of data to collect and risk scenarios to analyze. It’s a moving target, but FAIR analysis can keep defenders out in front.
More from the FAIR Institute: How to Factor Worst-Case Cyber Events into Risk Analysis