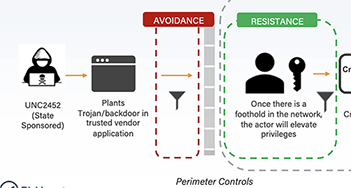
Prepare for the Next SolarWinds-style Attack with a Risk Model
Join RiskLens’ OnDemand webinar as our Risk Consultant, Sara Dominick, will talk through how to think about the SolarWinds incident and other related risks from a FAIR perspective. She talks through:
- How to quantify a cyber risk scenario like SolarWinds
- The benefits of quantitative risk-based planning for cybersecurity teams
- How to think about related threats from a FAIR perspective