 The Russian-speaking CL0P ransomware gang is on a tear exploiting zero-day vulnerabilities in the managed file transfer (MFT) solution MOVEit Transfer to steal data and extort hundreds of organizations from Siemens Electric to British Airways, the US Dept. of Energy, New York City school system and Johns Hopkins hospitals. CL0P previously broke in to Accellion File Transfer Appliance (FTA) devices in 2020 and 2021, and Fortra/Linoma GoAnywhere MFT servers in early 2023 with zero-day exploits.
The Russian-speaking CL0P ransomware gang is on a tear exploiting zero-day vulnerabilities in the managed file transfer (MFT) solution MOVEit Transfer to steal data and extort hundreds of organizations from Siemens Electric to British Airways, the US Dept. of Energy, New York City school system and Johns Hopkins hospitals. CL0P previously broke in to Accellion File Transfer Appliance (FTA) devices in 2020 and 2021, and Fortra/Linoma GoAnywhere MFT servers in early 2023 with zero-day exploits.
If your organization uses MOVEit or another file transfer service or indeed any trusted third-party ven(dor platform, you’re likely getting questions from the board on down, asking “what’s our risk?” With some basic risk quantification strategies from FAIR™ (Factor Analysis of Information Risk) and quantitative cyber risk analysis on the RiskLens SaaS platform, you can answer their questions in non-technical, business terms.
 Jacqueline Lebo is a Senior Risk Consultant for RiskLens. Learn more about professional consulting services at RiskLens.
Jacqueline Lebo is a Senior Risk Consultant for RiskLens. Learn more about professional consulting services at RiskLens.
Follow these steps, to analyze risk from the MOVEit Transfer vulnerability
First, you are going to want to understand the vulnerabilities (CVE-2023-34362, CVE-2023-35036, CVE-2023-35708), The MOVEit Transfer web application is vulnerable to a SQL injection that could allow an unauthenticated attacker to access MOVEit Transfer's database. For this to impact your organization, you will need to be using MOVEit to move sensitive documents. The threat actor is going to a malicious third party looking to exploit the vulnerability.
Second, it’s important to identify what type of data is being transferred. Let’s say you are a large healthcare organization that uses MOVEit to transfer PHI records back and forth for the purposes of diagnosis.
Third, you will need to take all this information and scope out a risk scenario:
“Quantify the risk of a malicious third party exploiting the MOVEit Transfer vulnerability to exfiltrate PHI data from the MOVEit Transfer database.“
Fourth, you can work through the RiskLens platform workshop using RiskLens data helpers designed by the RiskLens data science department to apply industry data on how frequently a threat actor would likely attempt to exploit your vulnerability in a common service such as MOVEit and to estimate how vulnerable you are (with compensating controls) to the MOVEit vulnerability exploit. The data helpers would also provide cost figures (based on industry norms or your corporate history) to respond to the data breach.
After working through the scenario, you will be able to understand how vulnerable you are to this type of attack and if this attack were to occur what your probable losses would be. This information can not only calm a nervous board of directors but also help you understand how to prioritize patching these important zero-day vulnerabilities.
RiskLens reporting on file transfer data breach risk
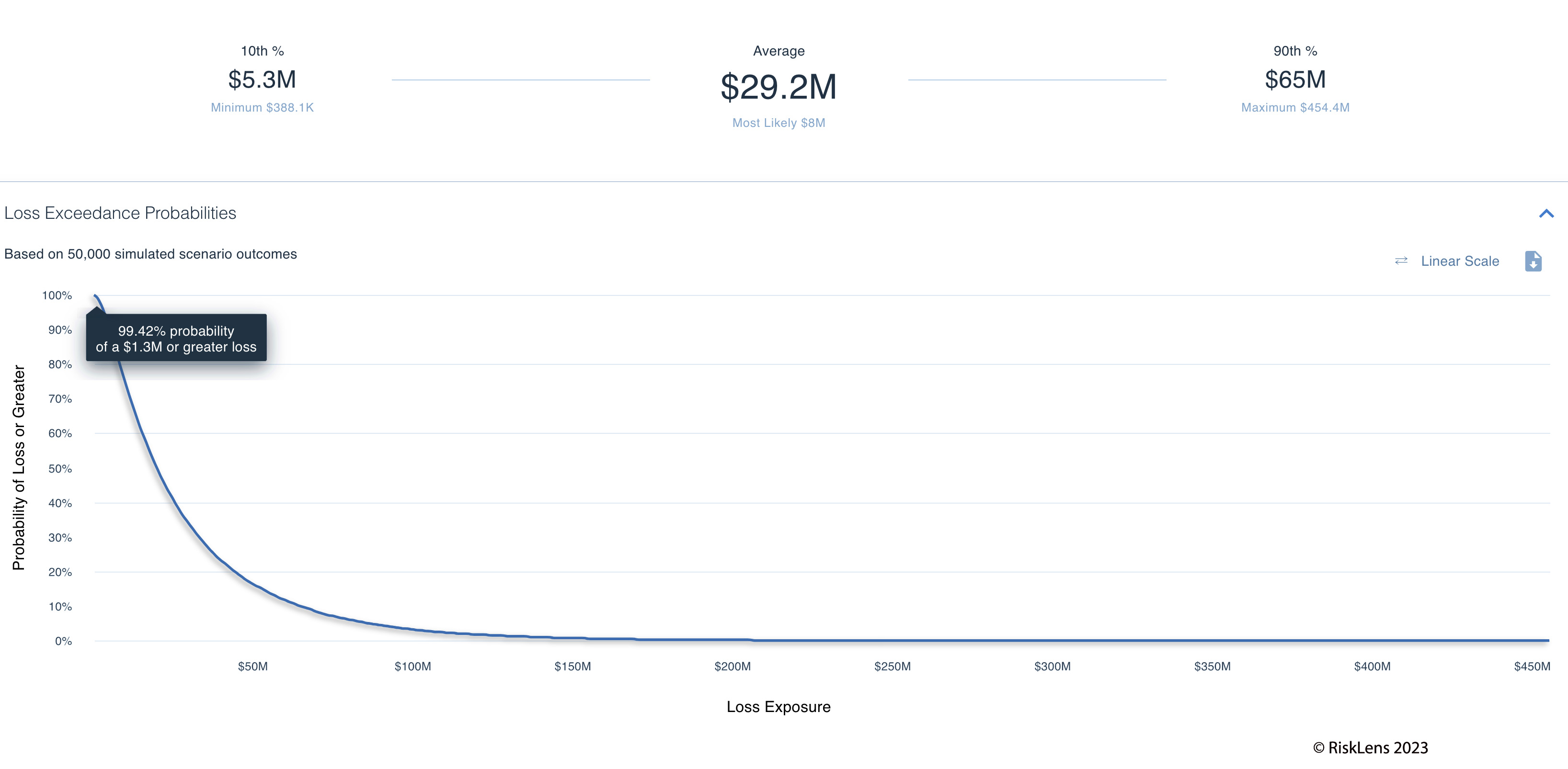
What you are seeing in this example of reporting from the RiskLens platform is an average annualized loss exposure of $29.2 million. This is a way of normalizing loss associated with several scenarios happening in a year. If you are interested in what this could look like if it were to happen once that average per event loss is closer to $11 million.

FAIR analysis with RiskLens reveals your key risk drivers, too – in this risk scenario, the record counts. We set the records count at one to 10 million. With this many records, we also have used industry average response efforts of 20-30 people for 40-320 hours each over the duration of the investigation.
Also, on the event frequency side, because this is a zero-day vulnerability, our estimate of the likelihood of successful attack (expressed as a percentage) will be higher knowing that this is out there reported and unpatched. The event frequency numbers are going to be largely based on industry data about this type of attack on a popular service such as MOVEit. These numbers can be tailored to your own organization’s threat intel as well.
How to use this risk analysis to plan your response to the MOVEit vulnerability or other zero-day attack on a third-party platform
1. You can use this data to weigh the cyber risk of this event versus the operational risk of turning off a platform like this and patching it.
2. You can understand how much your cyber insurance would cover your loss exposure.
3. You can use this data to prioritize patching this vulnerability vs. other risks.
4. You can use this data to communicate with business leaders who want to understand the risk in a quantitative manner to make some of the decisions detailed above
Learn more about ransomware risk analysis with the RiskLens platform in this blog post:
Big Game Hunting or Double Extortion Ransomware: Analyzing Complex Risk Scenarios with RiskLens