 A SOC report, following standards set by the accounting group AICPA, and particularly the SOC 2 Type 2 version, has become the market standard by which service organizations can build trust and confidence that their systems effectively protect customer information.
A SOC report, following standards set by the accounting group AICPA, and particularly the SOC 2 Type 2 version, has become the market standard by which service organizations can build trust and confidence that their systems effectively protect customer information.
According to AICPA, auditors for a SOC 2 Type 2 certification should verify that the organization has a risk assessment and management process in place to identify and mitigate risks. But AICPA doesn’t directly recommend a particular process.
Harris Moriarty is an Enterprise Account Executive and Rachel Slabotsky is a Sr. Manager Professional Services for RiskLens
But indirectly, it does. The AICPA “trust services criteria” for passing an audit (see them here) are based on the COSO framework, the most widely used framework for enterprise risk management. COSO recommends quantitative cyber risk analysis with FAIR™ (Factor Analysis of Information Risk, the internationally recognized standard for risk quantification) as a way for “management to align the cyber security program to the business objectives and set targets.”
While a risk management program based on FAIR on paper should impress the auditors, savvy companies use FAIR to make a SOC 2 Type 2 audit into more than a check-the-box exercise. They gain true business value by identifying their top risks for loss exposure in financial terms, and their most cost-effective mitigation tactics – and make better business-informed decisions as a result.
Learn FAIR risk assessment with training from the RiskLens Academy
How to Do a Risk Assessment for a SOC 2 Type 2 Report with FAIR
Here’s what a FAIR risk assessment for a SOC 2 Type 2 compliance audit looks like:
Step 1 – Scope the risk assessment
Every FAIR risk assessment starts with a careful definition of what we want to analyze, and the SOC guidelines make that scope clear; we’re concerned with protecting assets (such as databases or web applications within the defined system boundary of the SOC 2) from loss of some or all of the following (depending on the scope of the report being issued):
- Security
- Availability
- Processing Integrity
- Confidentiality
- Privacy
Step 2 – Define loss events
Next, we use that scope to define a set of risk scenarios (or loss events) we can analyze with FAIR, following the formula of a threat actor impacting each in-scope asset by some means, causing a loss, for example,
“Analyze the risk associated with a privileged insider intentionally disclosing the information contained in our customer relationship management database.”
The scenarios to analyze should be the most probable loss events to occur (based on your organization’s experience with loss or industry data) and the most probable to cause a significant loss. (This approach lines up with the recommendation in the trust principles [see page 23] to consider the significance of risks based on likelihood, impact, etc.).
Definition of a Risk Assessment from the AICPA Trust Services Criteria
 “Considers the Significance of the Risk — The entity’s consideration of the potential significance of the identified risks includes (1) determining the criticality of identified assets in meeting objectives; (2) assessing the impact of identified threats and vulnerabilities in meeting objectives; (3) assessing the likelihood of identified threats; and (4) determining the risk associated with assets based on asset criticality, threat impact, and likelihood.”
“Considers the Significance of the Risk — The entity’s consideration of the potential significance of the identified risks includes (1) determining the criticality of identified assets in meeting objectives; (2) assessing the impact of identified threats and vulnerabilities in meeting objectives; (3) assessing the likelihood of identified threats; and (4) determining the risk associated with assets based on asset criticality, threat impact, and likelihood.”
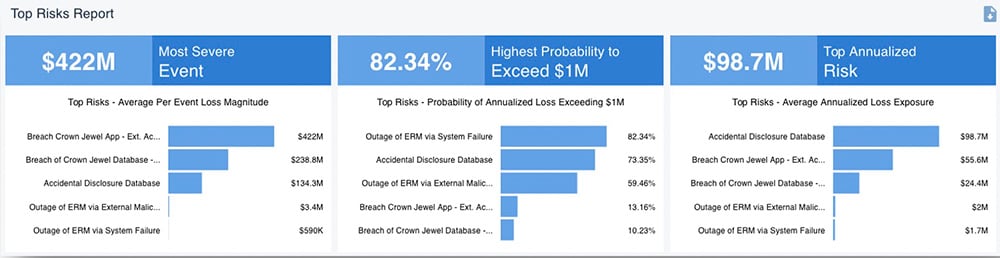 A RiskLens Top Risks report
A RiskLens Top Risks report
Step 3 Conduct a FAIR assessment
You can perform FAIR analysis on a sheet of paper or a spreadsheet, but for maximum credibility (and ease), the RiskLens SaaS platform automates the data entry and provides easy-to-use reporting to summarize the results.
RiskLens includes a Monte Carlo simulation engine that presents risk in a range of probable loss exposure in financial terms. Other features of the RiskLens platform relevant for SOC 2 Type 2 audits (and of high business value to your organization in the bargain): Rapid Risk Assessment for a quick look at the top risks of the organization, Top Risk Assessment for a deep dive into a single risk, and the capability to aggregate risk analyses for an overall assessment of loss exposure for a business unit, the organization as a whole or a particular function or information type (four kinds of audit reporting specified in the AICPA criteria). The platform also plots management’s risk tolerance levels against loss exposure (fulfilling another SOC criterion).
Step 4 Evaluate controls
Ultimately, the goal of the auditors for SOC 2 Type 2 is “evaluating the suitability of the design and operating effectiveness of controls,” as the trust services guidance says. With the Risk Treatment Analysis capability of the RiskLens platform, you can convincingly demonstrate the effectiveness of controls to reduce loss exposure in dollar terms for your in-scope risk scenarios – or, for that matter identify where controls are lacking or ineffective and take the most cost-effective steps to mitigate.
Step 5 Wrap it up in the reporting for a SOC evaluation
It’s the responsibility of the service organization to present the auditors with a description of its systems and controls and assert their effectiveness. It can be a time-consuming and difficult process overall, but the risk assessment piece of the documentation can be both speedy and authoritative, using FAIR and RiskLens – and pay off in actualized value for the business through accurate reporting.
See a FAIR risk assessment in action - Schedule a demo of the RiskLens platform