The Challenge
 Since the onset of the GDPR mandate, cybersecurity continues to be a top of mind for organizations handling personal data. The New York State Department of Financial Services DFS) with its Cybersecurity Regulation and the State of California with its Consumer Privacy Act, going into effect in 2020, are the tip of the spear in bringing GDPR-style data privacy protection rules to the States.
Since the onset of the GDPR mandate, cybersecurity continues to be a top of mind for organizations handling personal data. The New York State Department of Financial Services DFS) with its Cybersecurity Regulation and the State of California with its Consumer Privacy Act, going into effect in 2020, are the tip of the spear in bringing GDPR-style data privacy protection rules to the States.
The NYDFS Cybersecurity Regulation, which preliminarily went into effect in February, 2018, was further proof that regulators are continuing to raise the bar – particularly for financial institutions. Rather than simply stating that a cybersecurity risk assessment is required, the reporting procedures of the NYDFS Cybersecurity Regulation took it one step further, stating that the risk assessment must be sufficient to inform the design and maintenance of the cybersecurity program.
Since the guidance provided by the Cybersecurity Regulation is not overly prescriptive, the onus falls on the financial institutions to answer the question – does my heat map allow my organization to sufficiently address critical objectives such as:
- Identification, measurement and prioritization of the risks that are most important to business operations
- Cost-effective comparisons of risk remediation options, including proactive responses to said risks
- Effective communication of the posture of the cyber risk program to the Board and Senior Management who must sign off on the annual certification of compliance that is informed by the risk assessment
Rachel Slabotsky is Manager with the RiskLens Professional Services team
The Solution
Organizations are leveraging the RiskLens platform that operationalizes the FAIR™ (Factor Analysis of Information Risk) model to look beyond the minimum compliance requirements to help address the above requirements in a more meaningful way – measuring and communicating cyber risk in financial terms.
While risk quantification isn't yet a requirement for these standards, regulators are heading in that direction. In fact, the US Federal Banking Regulators (Federal Reserve, OCC, FDIC) recognized FAIR as a known model for cyber risk quantification in its Advanced Notice of Proposed Rulemaking on Enhanced Cyber Risk Management Standards. And a recent whitepaper from the Richmond Fed called out risk quantification with FAIR as a goal that financial institutions should work toward.
Below is an example of how a Fortune 500 Financial Institution effectively leveraged FAIR and RiskLens as the backbone to inform the design of their cybersecurity program to satisfy the reporting requirements of the NYDFS Cybersecurity Regulation and also improve their reporting to the Board.
Objective: Identify, measure and prioritize the risks that are most important to business operations
In order to effectively quantify risk, the FAIR model requires consistently defining scenarios based on assets, threats and loss effects. The organization leveraged this approach by identifying the most critical assets, the most likely threat actors, and the most probable and/or impactful ways in which the loss would materialize. To avoid temptation of analysis paralysis, the team grounded themselves around the objective at hand – informing the design of the cybersecurity program.
Once the most probable and impactful scenarios were identified, the list was prioritized with a small team of FAIR analysts and IT leaders with a wealth of knowledge of the business by triaging the risks. This exercise was completed over the course of a two-day Top Risk Identification Workshop using the RiskLens platform Triage function, led by experienced consultants from the RiskLens Professional Services team.
Once triaged, the top 20 scenarios were fully quantified in the RiskLens Cyber Risk Quantification (CRQ) platform. Figure 1 displays the comparison of top scenarios, with a range of probable outcomes (Note: Top 8 selected for graphical reporting purposes):
Figure 1: Top Risks
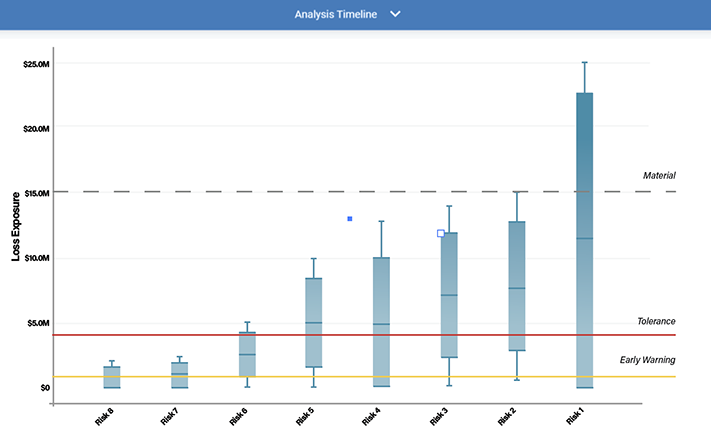
Objective: Provide cost-effective comparisons of risk remediation options in a proactive manner
Once the top risk scenarios were identified and quantified, the organization was able to leverage this information to start driving important decisions. For example, the organization was able to effectively determine which control areas (as specified by NYDFS) would have the most impact on the overall loss exposure from the top scenarios identified, measured in financial terms. For instance, the organization was able to demonstrate that a 20% improvement in activity monitoring controls would provide the greatest reduction in risk across key business assets.
Figure 2: Relative Risk Reduction by Service (with 20% effectiveness improvement)
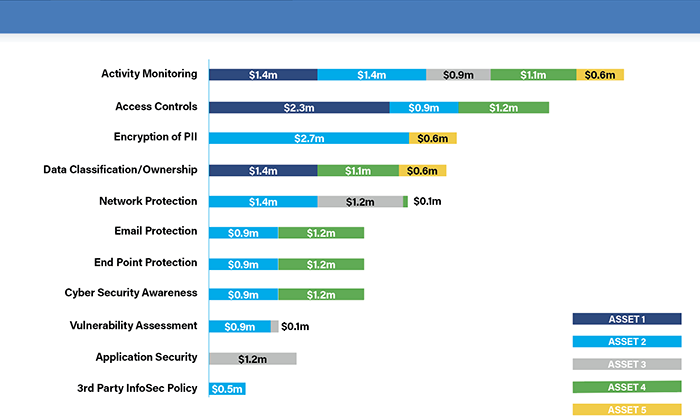
These top risk reduction opportunities were also brought to a strategy group to analyze the risk reduction opportunities against the annualized investment costs, which ultimately helps to drive prioritization of program efforts.
Objective: Effectively communicate the posture of the cyber risk program to the board and senior management
The NYDFS Cybersecurity Regulation elevated the responsibility for compliance to the board of directors and senior management because they are now required to sign off on the annual certification of compliance. For the risk analysts, the requirement worked to their advantage because the organization was able to effectively obtain buy-in from the board. Essentially, the analysts were able to leverage the NYDFS requirements as a catalyst to embed FAIR into their risk management program and quarterly reporting to the board.
Key Benefits
The FAIR standard already provides a practical foundation for quantifying cyber risk for many organizations, within the financial services sector and beyond. However, regulators are making it more challenging to effectively meet most of the requirements listed above without a formal risk quantification model and platform that allows you to assess and communicate cyber risk in financial terms.
Addressing risk in economic terms allows:
- Clear measurement of loss events that carry a "reasonable likelihood" of causing material harmPrioritization of mitigation efforts
- Justification of additional security investments and controls – including specific types of encryption
- Ability to communicate the impact that cyber risk has on business outcomes in a language that the business can understand, i.e., dollars and cents