 RiskLens has helped many of the world’s largest organizations launch and hit full stride on an enterprise-level cyber risk management program informed by FAIR™ risk quantification. In the process, we’ve learned the phases that successful programs pass through to get fully operationalized – and how to best support RiskLens customers along the way.
RiskLens has helped many of the world’s largest organizations launch and hit full stride on an enterprise-level cyber risk management program informed by FAIR™ risk quantification. In the process, we’ve learned the phases that successful programs pass through to get fully operationalized – and how to best support RiskLens customers along the way.
Two key learnings to keep in mind: 1) Expect FAIR (Factor Analysis of Information Risk) adoption to be a culture change and 2) you’ll ultimately win over the organization by showing how a quantified approach solves problems.
 Steven Tabacek is Co-founder & Chief Customer Officer of RiskLens. Read more by Steven: Quantitative Risk Reporting Stratification: Know Your Audience
Steven Tabacek is Co-founder & Chief Customer Officer of RiskLens. Read more by Steven: Quantitative Risk Reporting Stratification: Know Your Audience
Phase 1: Cultural Adaptation
The start of a risk quantification journey is always a cultural adaptation of risk quantification, leading the organization to accept that we are going to take an objective approach to measuring and reporting on risk. Organizations get so accustomed to quickly throwing a high/medium/low on risk with subjective assessments, that it can take time just to get people to accept that they can make objective decisions based on data that will result in more cost-effective decisions.
I recommend as a first step in education watching the video What Is Risk? The Bald Tire Scenario by Jack Jones, creator of FAIR, to quickly set out some basic concepts for the quantitative approach to cyber risk management. The next step for a risk analyst or CISO should be to take the FAIR Fundamentals training course from the RiskLens Academy; on completion of the course, add a FAIR certification for a highly sought-after job skill. Or, if already a RiskLens customer, learn by doing and start with the RiskLens platform training. Going forward, check the RiskLens and FAIR Institute blogs to continue education.
RiskLens Pro is a managed service that helps resource-strapped organizations stand up regular FAIR-based reporting and communication of cyber risk.
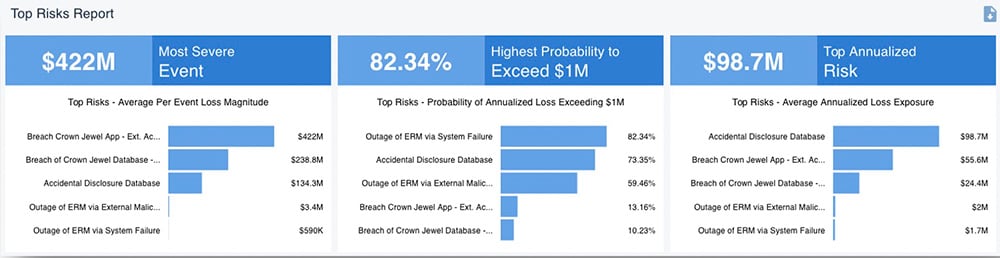
Top Risks Report from RiskLens Rapid Risk Assessment
Phase 2. Choose an Entry Point
Next you need an icebreaker to move along that cultural adaptation by showing people how quantitative risk analysis generates results. Most commonly, that’s a Rapid Risk Assessment with the RiskLens platform to identify the organization’s top risks. CISOs, the C-Level and Board like to see a baseline of top risks in relatable financial terms, and the platform can turn that around in an impressive 30 minutes or so. A top risks report also raises more questions than answers, a natural set-up for the next phase.
Phase 3. “Now that we have identified risk, what do we do with it?”
People like to solve problems. When they see an identified amount of risk, they take it as a challenge to brainstorm mitigation options from low-cost process changes to purchasing a cybersecurity controls tool. RiskLens Risk Treatment Analysis generates informative reports that compare these options in easy-to-read graphical presentations, clearly articulating the cost vs benefit. Most importantly, the analysis drives decision-making, and demonstrates the value of cyber risk quantification to the organization.
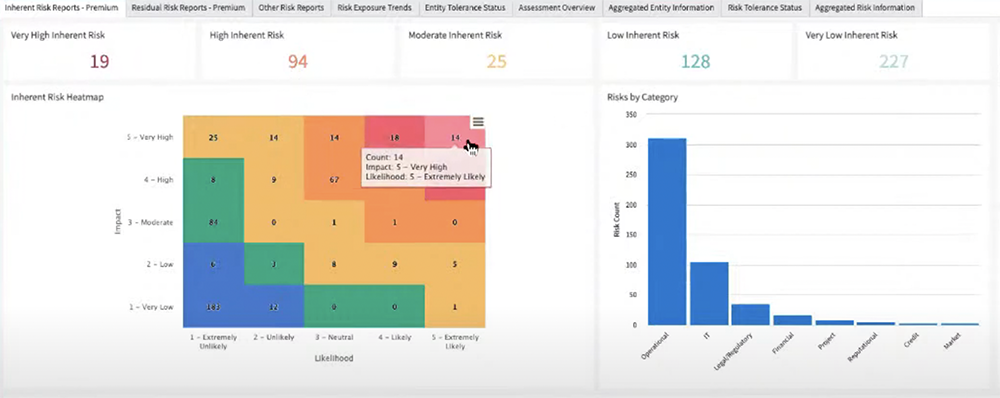 RiskLens Integration with ServiceNow GRC
RiskLens Integration with ServiceNow GRC
Phase 4. Risk Management Workflow Integration
With a cyber risk quantification program rolling, organizations begin to use CRQ for day-to-day decision support. Some common approaches:
- GRC Housecleaning
Re-phrasing risk register items in terms of a FAIR risk scenario with a threat, asset and impact eliminates vague items (like “the cloud” or “ransomware”) that aren’t really risks, just areas of concern.
Learn more: How to Get the Most Out of a GRC with RiskLens Quantitative Risk Analysis
- Organizing Analyses around Strategic, Operational and Tactical Decision-Making
We’ve seen new RiskLens clients get up to speed quickly (and persuade their organizations of the value of cyber risk quantification) with use cases, divided into three categories critical to any organization: Strategic (systemic risks that might be reported to the board, such as a major move to the cloud), Operational (such as prioritizing among controls investments) and Tactical (triage among everyday issues).
Learn more: Proven Use Cases to Start Quantitative Cyber Risk Management
New: RiskLens introduces Portfolio Management, highly flexible, automated reporting with dashboards customizable to the information needs of security and business leaders or the board
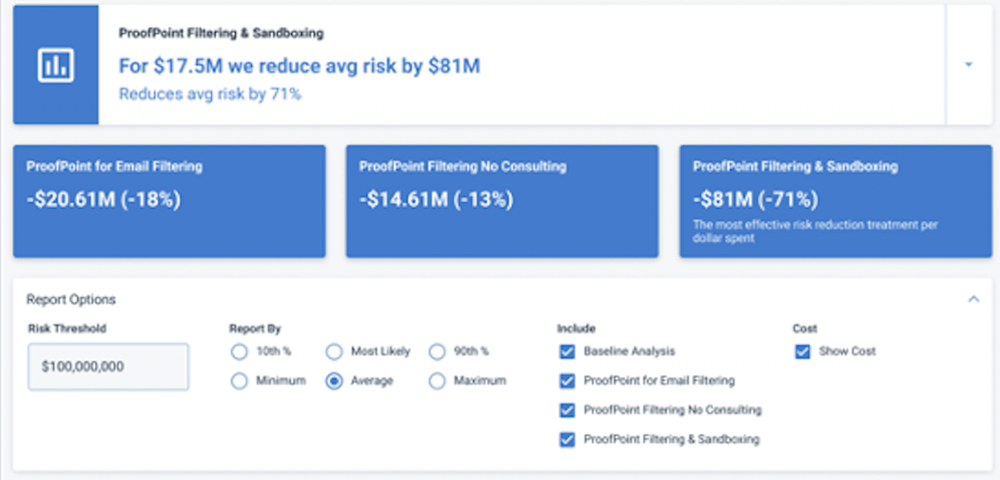
Cost/Benefit Analysis on the RiskLens Platform
- Ad Hoc Analysis on Emerging Threats
A cyber event at a competitor prompts the question from the C-suite, “what would be the impact if we suffered the same kind of attack?” Or a third-party web application goes down, and business leadership needs to know cost vs benefit of a workaround vs waiting for the vendor to restore service. A new demand for ad hoc, emergency analysis is always just around the corner, and the RiskLens platform supports quick reaction with features such as pre-packaged data libraries and risk scenarios, so analysts focus on data selection, not data collection.
Learn more:
Think Fast - Justify and Prioritize Cybersecurity Investment Decisions in an Hour
Reporting to the Board on Emerging Threats in Cybersecurity
Phase 5. Culture Change
Now that the organization has identified top risks, begun solving problems with Risk Treatment Analysis and integrated cyber risk quantification into the risk management workflow, a culture change follows. You’ll know it by the kinds of questions that stakeholders ask:
- Have we made improvements in that top risk analysis?
- Is risk trending down?
- Are we getting value out of the infosec investments we are making?
- Are we managing risk to acceptable levels?
- Are we exercising our fiduciary responsibility by understanding the risks on our crown jewel assets?
 To sum up the process of cyber risk quantification adoption: It starts with education, reveals top risks, finds an opening in use-case analysis, becomes embedded in workflow and results in a culture change.
To sum up the process of cyber risk quantification adoption: It starts with education, reveals top risks, finds an opening in use-case analysis, becomes embedded in workflow and results in a culture change.
Try cyber risk quantification for your industry with a free Industry Cyber Risk Report from RiskLens.