 The IT risk register: widely used but all too often ineffectively as a tool to track cybersecurity risks from identification through to risk mitigation.
The IT risk register: widely used but all too often ineffectively as a tool to track cybersecurity risks from identification through to risk mitigation.
The National Institute of Science and Technology, creator of the popular Cybersecurity Framework (NIST CSF), identified the root of the problem in its report Integrating Cybersecurity and Enterprise Risk Management (NISTIR 8286): “Most enterprises do not communicate their cybersecurity risk guidance or risk responses in consistent, repeatable ways.”
As the NIST report says, a cybersecurity risk register should be a tool (whether delivered as part of a GRC or IRM solution, a dashboard or a simple spreadsheet) to
- Aggregate risks
- Normalize risks so they can be compared
- Prioritize risks so the organization can choose which ones to address
In reality, many organizations use their risk registers as dumping grounds for, general topics of concern (“the cloud”, “phishing”), the latest vulnerability in the headlines, audit findings, policy exception requests and other items that at least have one thing in common: They are not really risks.
IT Risk Register Entries Should Be Risk Scenarios
The NIST document 8286 gives cyber risk register examples such as this:
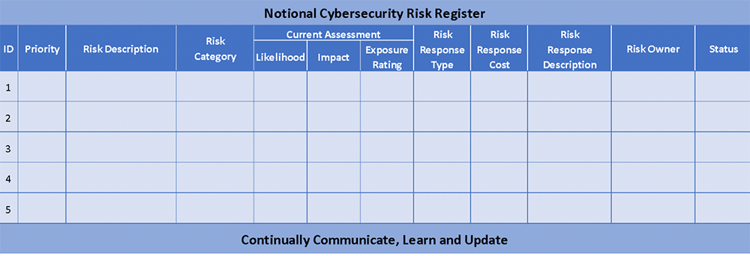
Taking a look at those center-left categories, NIST is recommending that every risk recorded can be defined by its likelihood and impact
That’s in line with the output of Factor Analysis of Information Risk (FAIR™) quantitative cyber risk analysis (the RiskLens platform is built for FAIR analysis)
In FAIR, every analysis starts with a risk description or scenario that defines the Who, What, When, Where and How of a threat actor attacking an asset resulting in a loss. In other words, what makes a risk a risk. Example:
“A malicious privileged insider impacting the confidentiality of the PII contained in the crown jewel database via misuse of their access.”
For a deeper dive, watch this video from the FAIR Institute:
How to Turn Your Risk Register Items into Risk Scenarios You Can Quantify with FAIR
Lean how FAIR quantitative risk analysis can help your organization better prioritize your cybersecurity risk program. Contact RiskLens.
From that well-defined starting point, risk analysts can gather likelihood and impact data (frequency and magnitude in FAIR terminology) that can be quantified and analyzed to produce a range of probable loss exposure for that risk. The NISTIR 8286 document specifically recommends FAIR as one of the methodologies to accomplish this analysis.
Describing risks by risk scenarios is a great starting point, but the RiskLens platform and FAIR analysis provides more functionality to get the most use from an IT risk register or GRC.
Optimizing a Cybersecurity Risk Register with RiskLens
Clean-up and optimization of a risk register is the first project many RiskLens clients tackle with the platform. It’s a two-step process:
- Translate the organization’s perceived top risks into risk statements
- Run those risks through the platform’s Rapid Risk Assessment capability to quickly prioritize the risks based on probable loss exposure.
Read more about the Rapid Risk capability.
Top Risks Report from RiskLens
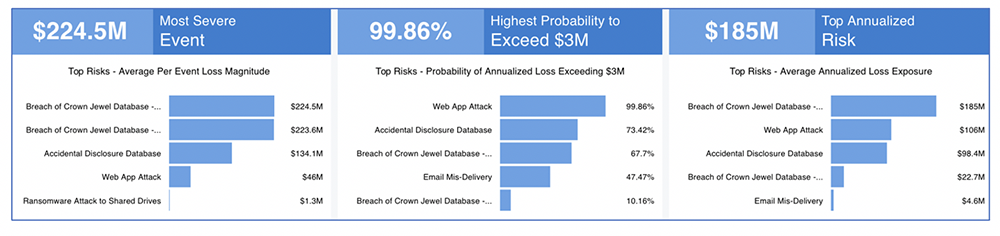
With risks prioritized in the register for impact, the next step is a detailed analysis on the platform of the highest risks to reveal the key drivers of risk, a strong indication on the most effective mitigations to choose. Then RiskLens clients use the Risk Treatment Analysis capability of the platform to compare mitigations for their effectiveness in reducing probable loss exposure in dollar terms.
RiskLens Integrates with IT Risk Registers
RiskLens has partnered with RSA, MetricStream, LogicGate and ServiceNow to offer risk quantification for risk register prioritization as seamless functionality. For an example, watch this video on the RiskLens-ServiceNow integration to see how register entries can be pulled into the RiskLens platform for analysis, and exported back to the GRC:
Video Introduction to the RiskLens Platform for ServiceNow GRC Users
Risk reporting integration with ServiceNow GRC
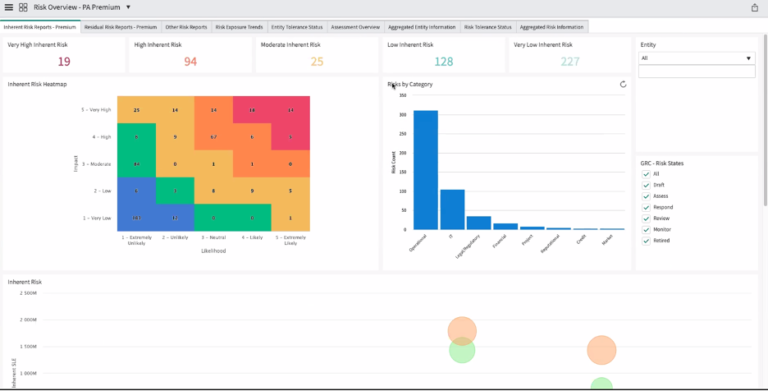
Also, RiskLens offers a Data Export API for executive dashboards or other custom risk reporting formats that keep clients up to date on their latest risk landscape.