Since 2011, the team at RiskLens has worked with organizations from nearly every market vertical implementing cyber risk quantification programs. We have experienced many successes and learned many lessons.
Customers expect RiskLens to bring this experiential basis into their organization, to ensure that the adoption and the maturity of a risk quantification program is efficient and effective. This article is pertinent for organizations that have selected both FAIR as their standard risk quantification model, and RiskLens' Cyber Risk Quantification (CRQ) as their risk analysis application.
Recognizing that many RiskLens customers have invested substantial time developing their own custom adoption programs, this article is intended to enhance existing programs as well as to develop new ones. After many years of successful customer engagements, the RiskLens team has observed five unique phases of CRQ Adoption and Maturity. 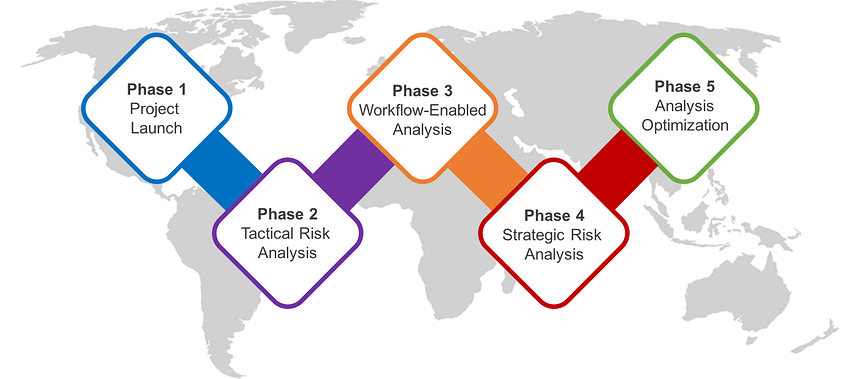
Phase 1: Project Launch
In this phase, we are assuming that an organizational need has been clearly defined requiring cyber risk quantification; a vision and strategy have been considered; and C-level, VP/manager, and risk analysts have conceptually bought in to FAIR and the RiskLens CRQ. The two primary tasks under Phase 1 include Training and Application Onboarding.
Training: RiskLens' onsite FAIR Certified training has proven to be most effective. After only three days of training, an analyst with critical thinking skills is generally equipped to perform simple risk analyses and generate useful reports.
Obviously, additional training and working with RiskLens consultants will further enhance the efficiency and capability of your risk team. To determine how many analysts may be necessary to fulfill your risk analysis objectives, consider reading “ Right-Size Your Cyber Risk Team in 4 Steps”.
Application Onboarding: CRQ provides pre-populated, out-of-the-box libraries for Asset Class, Threat, and Loss Tables, which greatly simplifies initial set-up and configuration. We recognize that each organization has unique assets, threats, and loss factors, so the RiskLens engineers have an extremely efficient process for customizing these libraries to match the operating characteristics of your organization.
RiskLens can be implemented and serviceable within one week for small organizations, two weeks for midsize, and three weeks for larger organizations. “Serviceable” is defined as the ability for an analyst to scope a risk scenario, collect/enter data, and generate useful reports. The time-frame I noted does not include the scoping of complex, enterprise-level assessments or integration into corporate processes. Evan Wheeler with the FAIR Institute wrote a blog that complements this topic titled “ Beginning Your Risk Journey with FAIR.”
Phase 2: Tactical Risk Analysis
Okay, so your analysts are trained, your Cyber Risk Quantification platform is configured and serviceable, and you’re wondering, what’s next…? This is where the rubber meets the road and it’s time to start analyzing risk and providing value.
Most organizations start out with single-scenario tactical risk analysis themes. Your analysts (on their own or with the help of RiskLens consultants) will scope tactical risk scenarios, collect/enter data, and generate useful risk analysis reports.
Listed below are examples of tactical risk analyses:
- Risk assessment – Migration of system to the cloud
- Risk assessment - Web app attacks, patching
- Risk assessment - Effect of act of terror, sabotage
- Cost-benefit analysis - Improved application patching
- Cost-benefit analysis - DLP improvements
- Cost-benefit analysis - Data encryption
- Comparative analysis - Ransomware / malware events
- Comparative analysis - Improved/additional controls
- Comparative analysis - Anti-phishing controls efficacy
Phase 3: Workflow-Enabled Analysis
Following efficiency and effectiveness gains realized in Phase 2, organizations typically transition into workflow-enabled analysis. For larger organizations, it typically starts with utilizing their existing GRC system qualitative “triage” of risk findings, and then using quantitative risk analysis for assessing meaningful risk scenarios.
Listed below are examples of a few workflow/"policy-driven” analyses:
- Analysis of all audit findings, MRA’s, MRIA’s
- Analysis of all “high” risk designated findings
- Analysis of Policy Exceptions and Risk Accept Determinations
- Business Impact Analysis (BIA’s) for critical systems
Phase 4: Strategic Risk Analysis
Strategic risk analyses are typically driven by boards and C-level executives with the intent of understanding, communicating, and managing cyber risk holistically and from a business perspective. This enables: executives to define their risk appetite and for boards to approve it; to right-size security budgets; prioritize risk mitigation initiatives; optimize cyber insurance coverage; as well as accept certain levels of risk.
Strategic risk analyses conducted with RiskLens also enable the measurement and risk trending over time, as well as conducting ROI analyses to assess the effectiveness of security investments.
Listed below are some examples of strategic risk analyses:
- Board Reporting – Analysis of “Top-10” risks
- Internal/External Audit – Enterprise Risk Assessment
- Budgeting – Analysis of Top Projects
Phase 5: Analysis Optimization
Analysis optimization is a very advanced phase and is usually applicable to customers that routinely use CRQ for tactical cyber risk analyses. The main concept behind Phase 5 is to optimize the analysis process for efficiency, leveraging well-defined data sources.
An analysis utilizing well-defined data sources is a potential candidate for future automation. It is commonplace for technology-centric CISO’s, managers, and analysts to want to “automate” risk analysis utilizing data from their security tools. This is a highly-technical topic, and if you’re interested in learning more, I recommend you register at the FAIR Institute and participate in the FAIR Data Integration group. The FAIR Data Integration Workgroup is a unique opportunity to join Jack Jones, Chairman of the FAIR Institute, Sounil Yu, SVP at Bank of America and other Institute members to discuss and collaborate on the development of standard data integration strategies allowing the transfer of data between security products and other risk mitigation tools and FAIR-based risk management software. Together, we will create the standard FAIR data integration requirements that will help the industry move closer to managing information risk in real-time.
Summary
The Adoption and Maturity phases noted in this blog are only intended to illustrate observed milestones of organizations that have implemented a Cyber Risk Quantification program based on FAIR, through the use of the RiskLens software.
Obviously, Phase 1, Training and Application Onboarding is required to start the process. It is not necessary for Phases 2-4 to be sequential. Strategic initiatives, driven by the board and/or management have been the catalyst of accelerated adoption for some RiskLens customers.
Whether you have urgent business reporting requirements, need to make difficult budget decisions, need to meet new regulatory requirements, or need to resolve some high-profile audit findings, RiskLens can efficiently and effectively help you jumpstart your cyber risk quantification program.
If you’re a current RiskLens customer, feel free to contact me directly for additional information. If you’re a prospective customer and would like to learn more about our software and services, contact us here.